Apr 7, 2020
Multiplexed single-molecule enzyme activity analysis for counting disease-related proteins in biological samples
Posted by Quinn Sena in category: biotech/medical
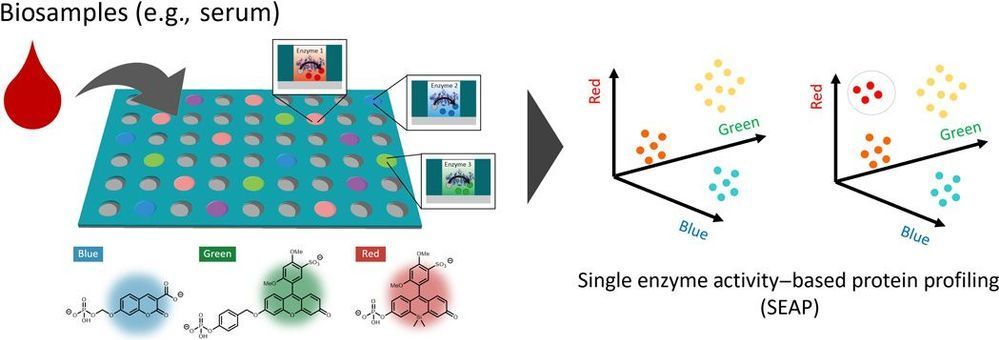
We established an ultrasensitive method for identifying multiple enzymes in biological samples by using a multiplexed microdevice-based single-molecule enzymatic assay. We used a paradigm in which we “count” the number of enzyme molecules by profiling their single enzyme activity characteristics toward multiple substrates. In this proof-of-concept study of the single enzyme activity–based protein profiling (SEAP), we were able to detect the activities of various phosphoric ester–hydrolyzing enzymes such as alkaline phosphatases, tyrosine phosphatases, and ectonucleotide pyrophosphatases in blood samples at the single-molecule level and in a subtype-discriminating manner, demonstrating its potential usefulness for the diagnosis of diseases based on ultrasensitive detection of enzymes.
Cellular functions are mediated by the activities of diverse enzymes, and hence, determining the functional changes that occur in these enzymes during pathogenesis is crucial for understanding and detecting diseases (1). However, the detection sensitivity of conventional assays for discovering and using enzyme biomarkers for diagnosis needs to be improved. In case of DNA and RNA analysis, enhancing the sensitivity of detection to the single-molecule level has revolutionized biomarker discovery and usage (2). However, the detection methods for proteins, which are thought to contain more functionality-oriented information that can be directly linked to the phenotypes, are yet to attain such a high degree of sensitivity (3).
In this study, we developed a novel assay platform for comprehensively detecting multiple enzymes in biological samples at single protein level for ultrasensitive and quantitative profiling of the disease-related enzymatic activities. This method is based on single-molecule enzyme analysis performed in a microfabricated chamber device, in which single-molecule enzymes in a diluted biological sample are separately loaded into individual microchambers for measuring and detecting its activity (4, 5). Although conventional single-molecule analysis is commonly used to study the biochemical properties of specific enzymes, their application for analyzing biological samples containing complex mixtures of characterized and uncharacterized proteins remains challenging, as it is difficult to predict which enzyme is loaded into each chamber due to random distribution.