ZeroDayRAT is a cross-platform mobile spyware sold on Telegram that enables live surveillance, OTP theft, and financial data theft on infected devices




A new commercial mobile spyware platform dubbed ZeroDayRAT is being advertised to cybercriminals on Telegram as a tool that provides full remote control over compromised Android and iOS devices.
The malware provides buyers with a full-featured panel for managing infected devices, reportedly supporting Android 5 through 16 and iOS up to version 26 latest.
Researchers at mobile threat hunting company iVerify say that ZeroDayRAT not just steals data but also enables real-time surveillance and financial theft.

It’s a typical workday and you sign onto your computer. Unbeknownst to you, a high-frequency sensing system embedded in your work device is now tracking your heart rate, allowing your employer to monitor your breaks, engagement, and stress levels and infer alertness. It sounds like a dystopian scenario, but some believe it’s not so far from current reality.

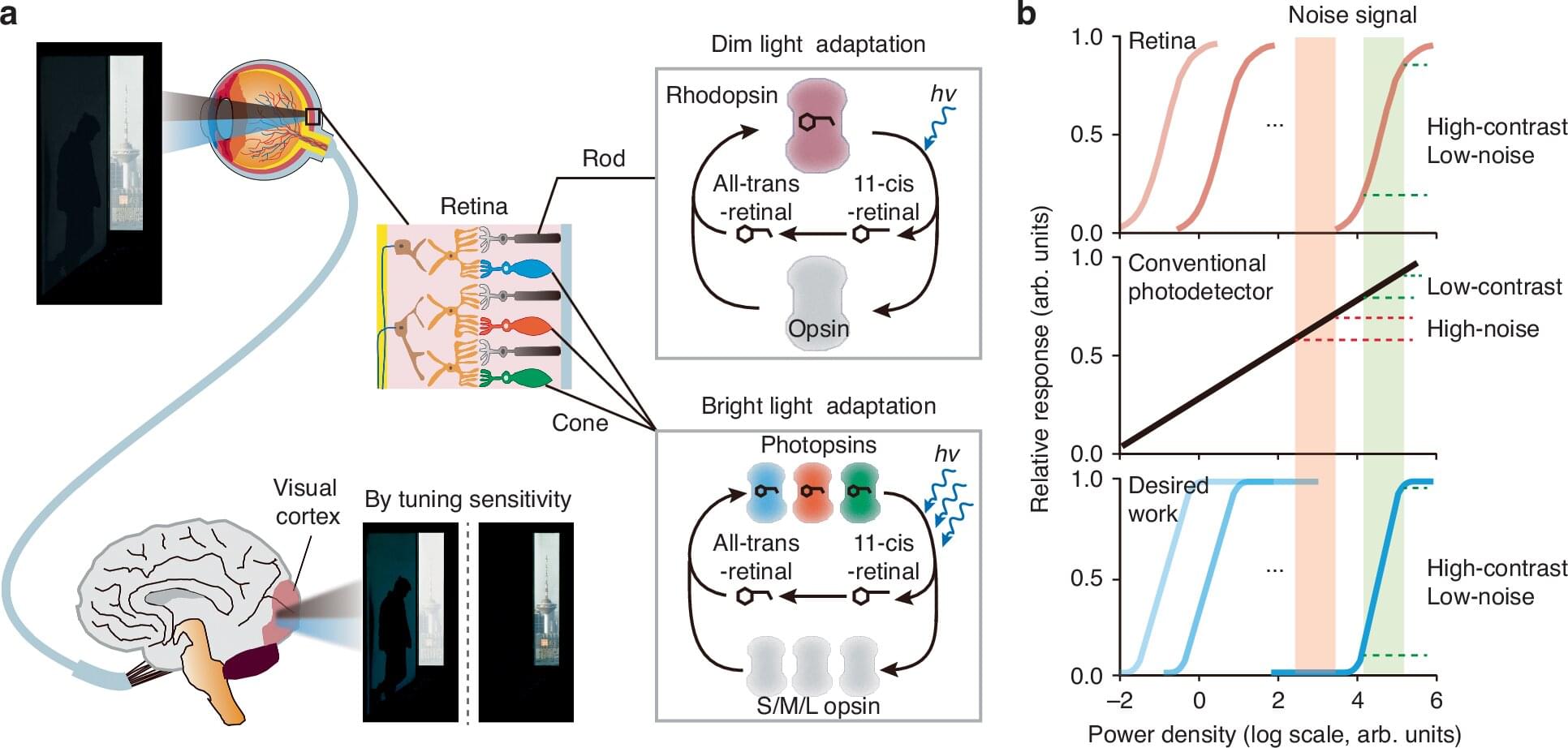
Drawing inspiration from the remarkable adaptability of the human eye, researchers from the Institute of Metal Research (IMR) of the Chinese Academy of Sciences have developed a novel phototransistor with tunable sensitivity.
This breakthrough provides an efficient solution for detecting low-contrast targets in complex visual environments, which is a critical challenge for advanced machine vision systems in applications such as precision guidance and smart surveillance.
The results are published in Light: Science & Applications.

Basically every year 1 billion people get infected by influenza causing extreme resource shortages still it is getting better to keep the death count down with vaccines but still its potential is still very dangerous and is not quite contained. Along with the super k version of influenza causing a spike in cases globally now. I still think that we need better protection against certain diseases so the resources are not drained globally. Perhaps we can use tricorder like devices on our phones that essentially heal us from diseases which I believe radio nanotransfection could lead to breakthroughs in the future.
Credit: WHO / Lindsay Mackenzie.
Influenza, or the flu, is both a seasonal and a pandemic virus. Every year, mainly during the winter season, seasonal influenza infects as many as 1 billion people. This makes it one of the most common infectious respiratory viruses, after the common cold. Thankfully, the WHO Global Influenza Surveillance and Response System, or GISRS, monitors what viruses are circulating and twice a year recommends which viruses to target in the flu vaccine for the upcoming season. The flu vaccine is the best way to prevent infection and may reduce symptoms if you do get the flu. For those who are more vulnerable to flu, what we call ‘high risk groups’, the vaccine can save your life. Good hygiene practices can also reduce the risk of infection (for more information, see the factsheet here ). Thankfully, although there are hundreds of millions of cases every year, the vast majority of these are not serious. Nevertheless, WHO estimates that there are 3 to 5 million cases of severe illness and between 290 000 to 650 000 respiratory deaths annually.

This isn’t a high-security government facility. It’s Beverly Hills High School.
District superintendent Alex Cherniss says the striking array of surveillance tools is a necessity, and one that ensures the safety of his students. “We are in the hub of an urban setting of Los Angeles, in one of the most recognizable cities on the planet. So we are always a target and that means our kids are a target and our staff are a target,” he said. In the 2024–2025 fiscal year, the district spent $4.8 million on security, including staff. The surveillance system spots multiple threats per day, the district said.
Beverly Hills’ apparatus might seem extreme, but it’s not an outlier. Across the U.S., schools are rolling out similar surveillance systems they hope will keep them free of the horrific and unceasing tide of mass shootings. There have been 49 deaths from gunfire on school property this year. In 2024, there were 59, and in 2023 there were 45, per Everytown for Gun Safety. Between 2000 and 2,022,131 people were killed and 197 wounded at schools in the U.S., most of them children. Given those appalling metrics, allocating a portion of your budget to state of the art AI-powered safety and surveillance tools is a relatively easy decision.

