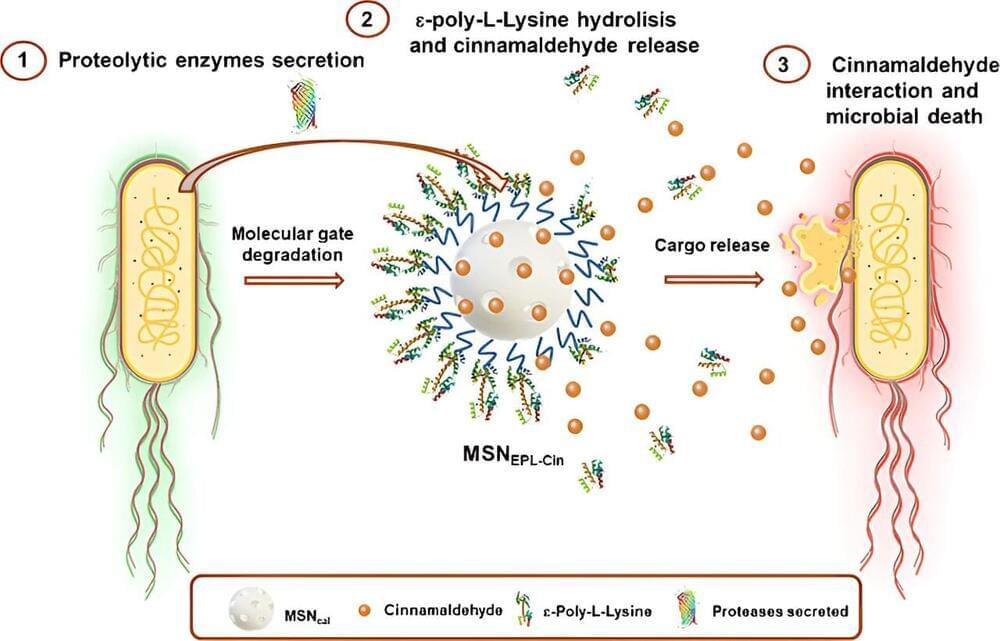
They found emissions of SO2 and NOx – both linked to increased asthma risk and a variety of other health issues – decreased by a total of 1m metric tons over that three-year period.
To determine the impact of that reduction on public health, the authors “used air quality models to track the population exposed to pollution from power plants”, Millstein said. They also employed epidemiological research to examine the effects of those emissions, and quantified the benefits by using an Environmental Protection Agency dollar value establishing the value of reducing the risk of early death across the population, he said.
All told, the emission reductions from SO2 and NOx provided $249bn of climate and health benefits to the US, the authors found – a figure Millstein said he found was “noteworthy”