Feb 19, 2016
Fujitsu develops new deep learning technology to analyze time-series data with high precision
Posted by Early Boykins III in categories: business, education, robotics/AI, wearables
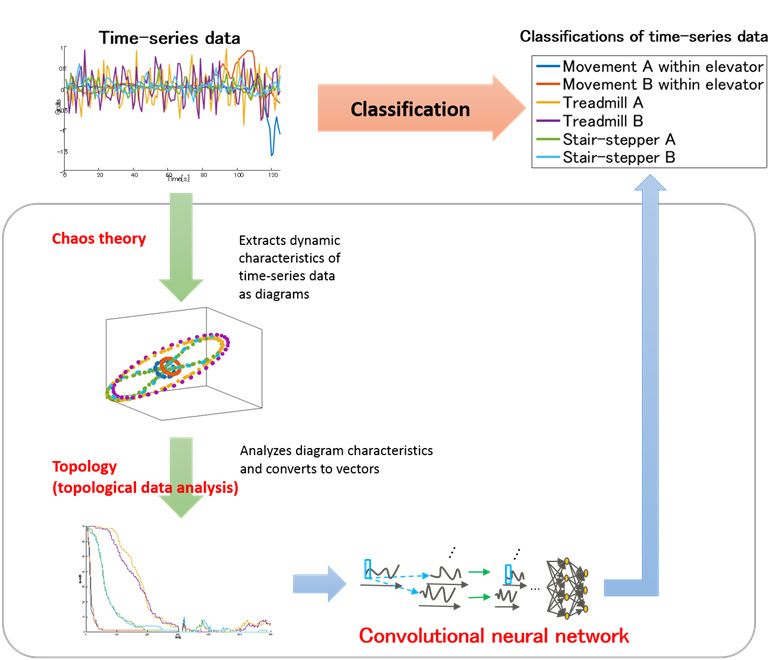
Fujitsu Laboratories today announced that it has developed deep learning technology that can analyze time-series data with a high degree of accuracy. Demonstrating promise for Internet-of-Things applications, time-series data can also be subject to severe volatility, making it difficult for people to discern patterns in the data. Deep learning technology, which is attracting attention as a breakthrough in the advance of artificial intelligence, has achieved extremely high recognition accuracy with images and speech, but the types of data to which it can be applied is still limited. In particular, it has been difficult to accurately and automatically classify volatile time-series data–such as that taken from IoT devices–of which people have difficulty discerning patterns.
Now Fujitsu Laboratories has developed an approach to deep learning that uses advanced mathematical techniques to extract geometric features from time-series data, enabling highly accurate classification of volatile time-series. In benchmark tests held at UC Irvine Machine Learning Repository that classified time-series data captured from gyroscopes in wearable devices, the new technology was found to achieve roughly 85% accuracy, about a 25% improvement over existing technology. This technology will be used in Fujitsu’s Human Centric AI Zinrai artificial intelligence technology. Details of this technology will be presented at the Fujitsu North America Technology Forum (NAFT 2016), which will be held on Tuesday, February 16, in Santa Clara, California.
Background