There is relatively little information on the long-term health effects of tattooing, but a couple of recent studies suggest the art form might trigger prolonged inflammation


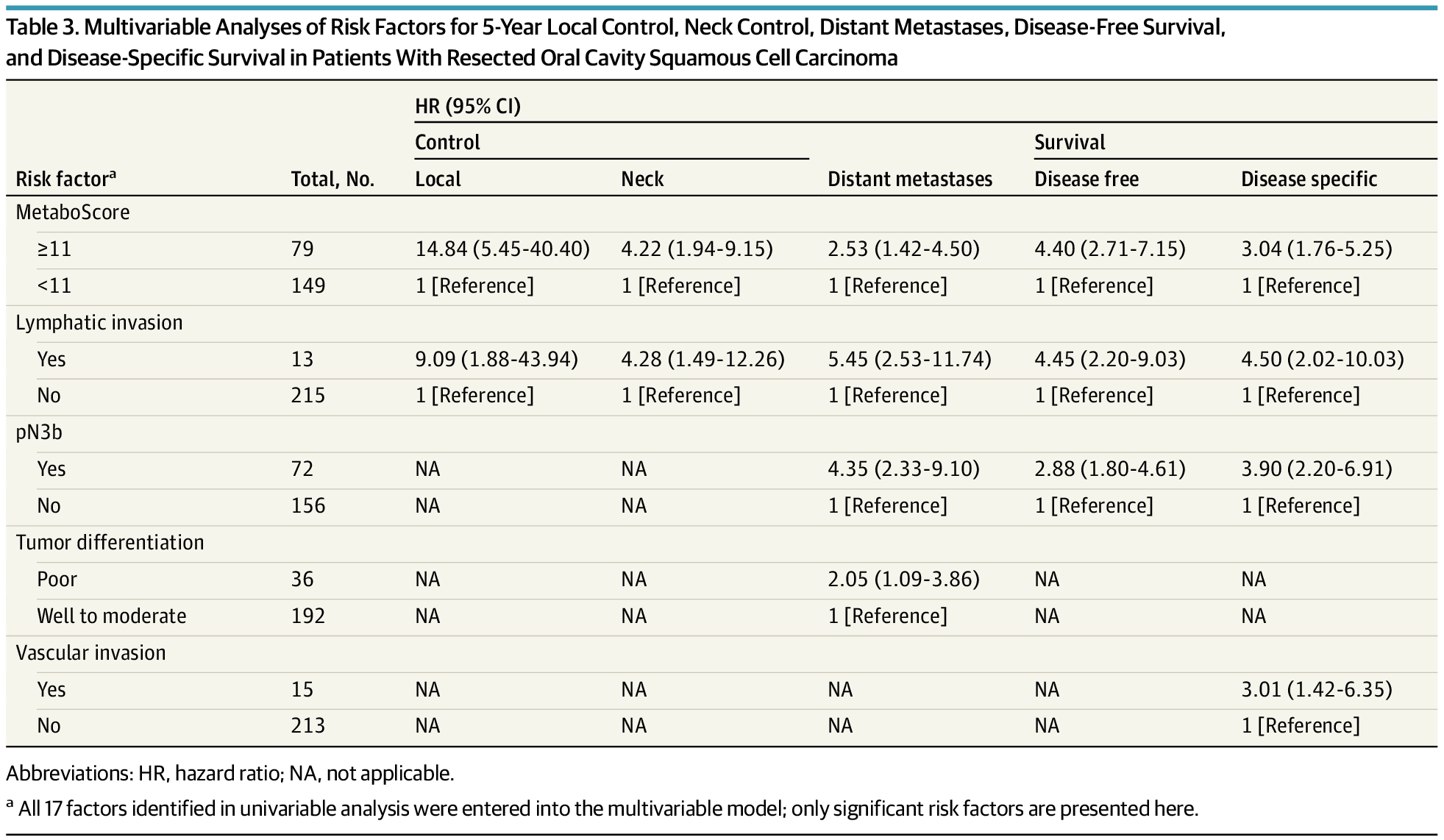
A cohort study developed and validated a serum metabolite-based prognostic scoring system (MetaboScore) to predict recurrence risk in oral cavity squamous cell carcinoma (OCSCC) among patients with resected, advanced-stage disease and high betel quid exposure.
The MetaboScore, comprising 19 metabolites, was independently associated with increased risk of local, regional, and distant recurrence, as well as lower disease-free and disease-specific survival, beyond conventional staging.
Importance Improved methods are needed to predict recurrence in oral cavity squamous cell carcinoma (OCSCC). However, to date, no metabolome studies have fully explored the prediction of OCSCC relapse patterns and survival.
Objective To identify serum metabolites associated with OCSCC recurrence and develop and validate a prognostic scoring system.
Design, Setting, and Participants This retrospective cohort study was conducted at a single tertiary academic center and enrolled patients with histologically confirmed, surgically resected first primary advanced-stage OCSCC from betel quid–chewing areas. Patients underwent primary surgery between February 2007 and May 2018, with follow-up data systematically collected through a prospectively maintained institutional registry. Data were analyzed from December 2024 to September 2025.




For 25 years, the NVIDIA Graduate Fellowship Program has supported graduate students doing outstanding work relevant to NVIDIA technologies. Today, the program announced the latest awards of up to $60,000 each to 10 Ph.D. students involved in research that spans all areas of computing innovation.
Selected from a highly competitive applicant pool, the awardees will participate in a summer internship preceding the fellowship year. Their work puts them at the forefront of accelerated computing — tackling projects in autonomous systems, computer architecture, computer graphics, deep learning, programming systems, robotics and security.
The NVIDIA Graduate Fellowship Program is open to applicants worldwide.

Researchers from the School of Physics at Wits University, working with collaborators from the Universitat Autònoma de Barcelona, have demonstrated how quantum light can be engineered in space and time to create high-dimensional and multidimensional quantum states. Their work highlights how structured photons—light whose spatial, temporal or spectral properties are deliberately shaped—offer new pathways for high-capacity quantum communication and advanced quantum technologies.
Published as a review article in Nature Photonics, the study surveys rapid progress in techniques capable of creating, manipulating and detecting quantum structured light. These include on-chip integrated photonics, nonlinear optics, and multiplane light conversion, which now form a modern and increasingly powerful toolkit. Together, these advances are bringing structured quantum states closer to real-world applications in imaging, sensing, and quantum networks.


The outer planets of the solar system are swarmed by ice-wrapped moons. Some of these, such as Saturn’s moon Enceladus, are known to have oceans of liquid water between the ice shell and the rocky core and could be the best places in our solar system to look for extraterrestrial life. A new study published Nov. 24 in Nature Astronomy sheds light on what could be going on beneath the surface of these worlds and provides insights into how their diverse geologic features may have formed.
“Not all of these satellites are known to have oceans, but we know that some do,” said Max Rudolph, associate professor of earth and planetary sciences at the University of California, Davis and lead author on the paper. “We’re interested in the processes that shape their evolution over millions of years and this allows us to think about what the surface expression of an ocean world would be.”
How geology works on icy moons From mountains to earthquakes, Earth’s surface geology is powered by the movement and melting of rock deep inside the planet. On icy moons, geology is driven by the action of water and ice.