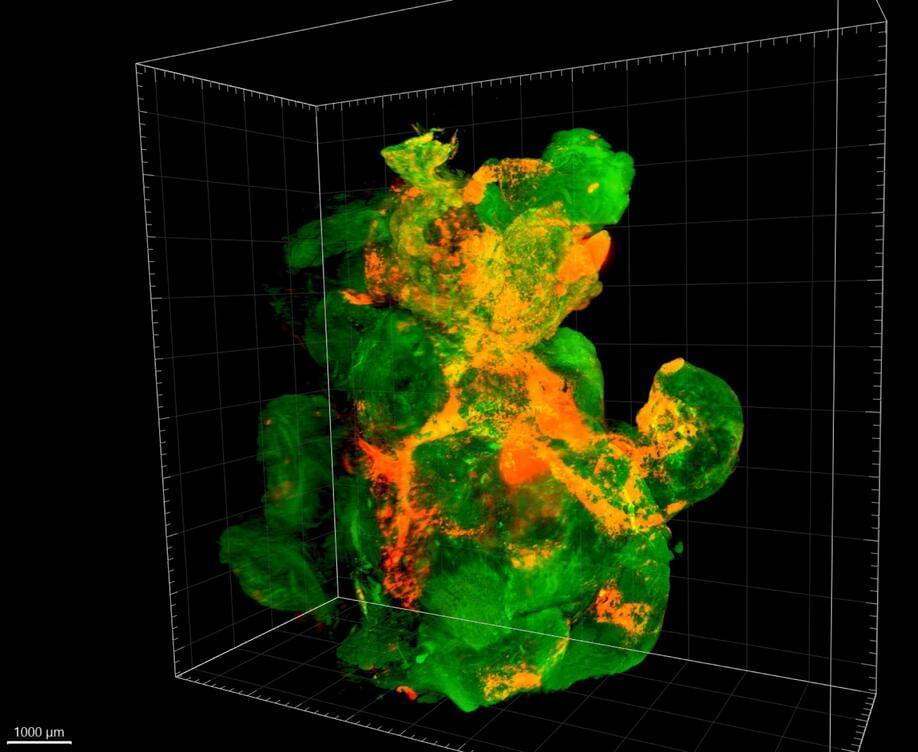
Pancreatic cancer is one of the deadliest types of cancers in humans. It is the fourth leading cause of cancer-related deaths in the western world. The early stages of the disease often progress without symptoms, so diagnosis is usually very late.
Another problem: Advanced tumors – and their metastases – can no longer be completely removed. Chemotherapies, in turn, attack not only the tumor cells but also healthy cells throughout the body. Innovative nanoparticles could be a new approach to treat cancer more precisely.
The approach was developed by a research team from the Max Planck Institute (MPI) for Multidisciplinary Sciences, the University Medical Center Göttingen (UMG), and the Karlsruhe Institute of Technology (KIT). The therapy is now to be optimized for clinical application as quickly as possible.