Anthropic, OpenAI and Google DeepMind score low on planning for catastrophic risks.



Real-time MRI-guided ventricular ablation was demonstrated as a technically feasible and safe approach, providing precise cardiac visualization without radiation.
This case report demonstrates the technical feasibility and safety of the first-in-human real-time magnetic resonance (MR)–guided radiofrequency ventricular ablation procedure for outflow tract premature ventricular complexes.

If you look across space with a telescope, you’ll see countless galaxies, most of which host large central black holes, billions of stars and their attendant planets. The universe teems with huge, spectacular objects, and it might seem like these massive objects should hold most of the universe’s matter.
But the Big Bang theory predicts that about 5% of the universe’s contents should be atoms made of protons, neutrons and electrons. Most of those atoms cannot be found in stars and galaxies—a discrepancy that has puzzled astronomers.
If not in visible stars and galaxies, the most likely hiding place for the matter is in the dark space between galaxies. While space is often referred to as a vacuum, it isn’t completely empty. Individual particles and atoms are dispersed throughout the space between stars and galaxies, forming a dark, filamentary network called the “cosmic web.”
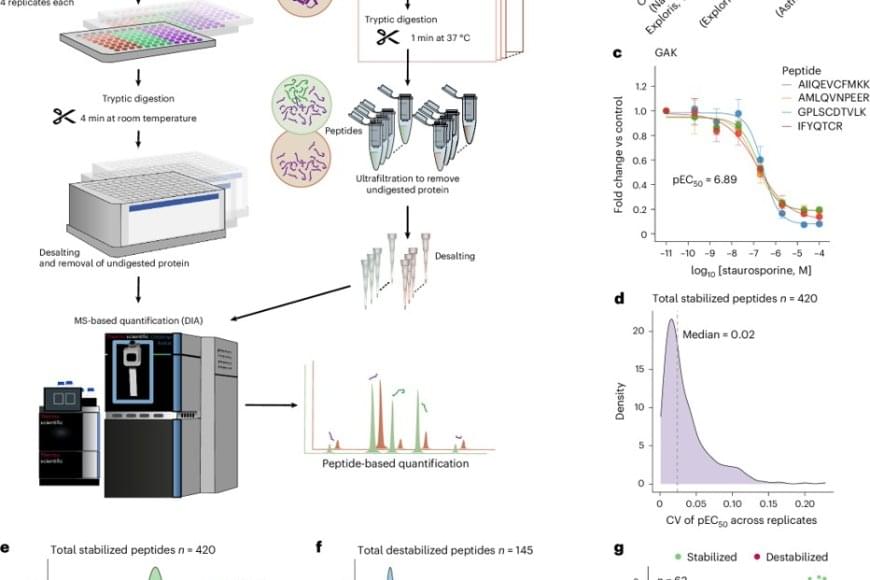
Long-known as the ‘workhorses of the cell,’ proteins are responsible for powering nearly every function in the body. Often critical to this is their interactions with other small molecules known as ligands. In a new study published in Nature Structural and Molecular Biology, the researchers introduce HT-PELSA, a high-throughput adaptation of an earlier tool that detects these interactions. This new tool can process samples at an unprecedented scale, a breakthrough that promises to accelerate drug discovery and our understanding of fundamental biological processes.
Still a fairly new tool itself, the original PELSA (peptide-centric local stability assay) method, launched last year by researchers identifies protein-ligand interactions by tracking how ligand binding affects protein stability. When a ligand binds to a protein, that part of the protein becomes more stable and less prone to the effects of enzymes like trypsin, which cuts proteins into smaller peptide fragments.
What made PELSA especially noteworthy was its ability to detect peptide-level changes in stability across the entire proteome – that is, across all of the proteins in an organism. Although effective, nearly every step in the PELSA workflow is done by hand, meaning scientists can only process a few samples at a time. This not only requires a lot of time and effort but also increases the risk of contamination and accidental error.
HT-PELSA streamlines this process significantly by shifting from full-size tubes to micro-wells. Such a change enables automation of PELSA’s steps and allows researchers to analyse hundreds of samples in parallel while maintaining the same sensitivity and reproducibility.
“Before, I could only do at most, maybe 30 samples per day,” said the first author of the study. “Now, with HT-PELSA, we can scan 400 samples per day – it has highly simplified the workflow”
While in PELSA, trypsin-cleaved peptides are separated from whole proteins based on their mass, HT-PELSA leverages the water-repellant nature of proteins. It utilises a surface that proteins stick to more readily than peptides, thus allowing the scientists to separate the two. This not only further automates the process, but also enables the detection of membrane proteins that, up until now, were hard or even impossible to study.
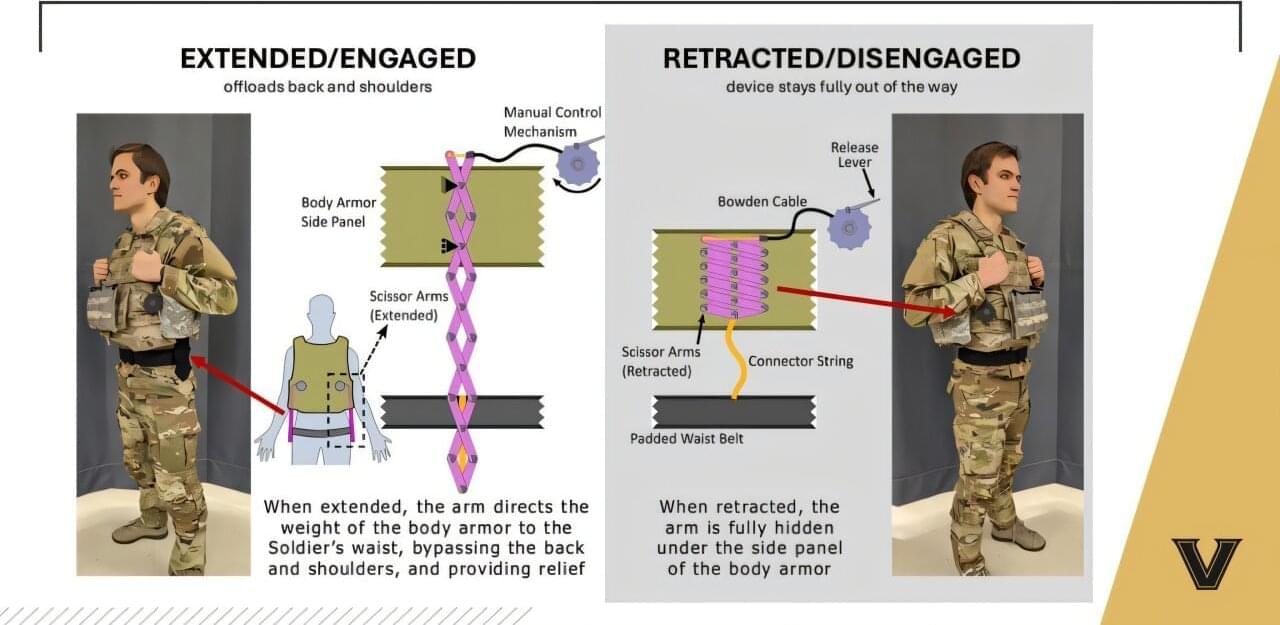
Vanderbilt researchers have developed a lightweight wearable device that shifts body armor weight off the shoulders and back of soldiers, helping reduce pain and injury risk.
A new study, “Wearable weight distribution devices for reducing injury risk: How varying amounts of body armor offloading affect biomechanics and comfort,” is published in the journal Applied Ergonomics.
The research study was led by Paul Slaughter, a recent Vanderbilt Ph.D. graduate, and Karl Zelik, associate professor of mechanical engineering. Slaughter and Zelik, in partnership with Vanderbilt senior research engineer Chad Ice, also filed a patent on this wearable weight distribution device.




“The most striking thing was the high dust levels,” said Dr. Eva Dock.
What risks can metal recycling pose to workers? This is what a recent study published in the International Journal of Hygiene and Environmental Health hopes to address as a collaborative team of researchers from Sweden investigated metal and dust exposure to recycling workers. This study holds the potential to help scientists, legislators, and the public better understand the risks of metal recycling as a means for enhancing green technologies.
For the study, the researchers analyzed observation and questionnaire data obtained from 139 recycling workers across 13 Swedish metal recycling companies. Additionally, the team obtained dust and metal samples to ascertain employee exposure and biological samples, including blood and urine, to ascertain individual metal and dust exposure. The goal of the study was to ascertain the efficacy of safety protocols and the severity of exposure to employees.
In the end, the researchers discovered alarming results, including 19 percent of the employees discovered to have heightened levels of more than 10 metals within their body and 94 having heightened levels of six metals. Of the 139 employees, 32 percent were involved in e-waste recycling, while safety protocols to mitigate dust exposure were discovered to be less than satisfactory, specifically regarding the use of respiratory equipment or hygiene protocols.

Benjamin D. Humphreys provides an Editor’s Note on Christine V. Behm et al. https://doi.org/10.1172/JCI197807
The figure from Behm et al. shows nephrocalcinosis in older kidney-specific Cldn2-KO mice.
Deposits of hydroxyapatite called Randall’s plaques are found in the renal papilla of calcium oxalate kidney stone formers and likely serve as the nidus for stone formation, but their pathogenesis is unknown. Claudin-2 is a paracellular ion channel that mediates calcium reabsorption in the renal proximal tubule. To investigate the role of renal claudin-2, we generated kidney tubule–specific claudin-2 conditional KO mice (KS-Cldn2 KO). KS-Cldn2 KO mice exhibited transient hypercalciuria in early life. Normalization of urine calcium was accompanied by a compensatory increase in expression and function of renal tubule calcium transporters, including in the thick ascending limb. Despite normocalciuria, KS-Cldn2 KO mice developed papillary hydroxyapatite deposits, beginning at 6 months of age, that resembled Randall’s plaques and tubule plugs.