Terahertz (THz) radiation is electromagnetic radiation ranging from frequencies of 0.1 THz to 10 THz, with wavelengths between 30μm and 3mm. Reliably detecting this radiation could have numerous valuable applications in security, product inspection, and quality control.
For instance, THz detectors could allow law enforcement agents to uncover potential weapons on humans or in luggage more reliably. It could also be used to monitor natural environments without damaging them or to assess the quality of food, cosmetics and other products.
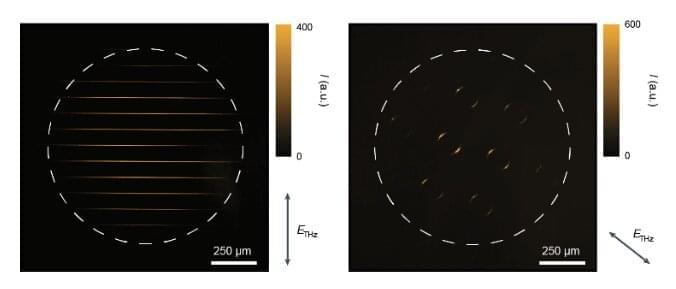
Recent studies introduced several devices and solutions for detecting terahertz radiation. While a few of them achieved promising results, their performance in terms of sensitivity, speed, bandwidth and operating temperature is often limited. Researchers at Massachusetts Institute of Technology (MIT), University of Minnesota, and other institutes in the United States and South Korea recently developed a new camera that can reliably detect THz radiation at room temperature, while also characterizing its so-called polarization states. This camera, introduced in a paper published in Nature Nanotechnology, is based on widely available complementary metal-oxide-semiconductors (CMOS), enhanced using quantum dots (i.e., nm-sized semiconductor particles with advantageous optoelectronic properties).