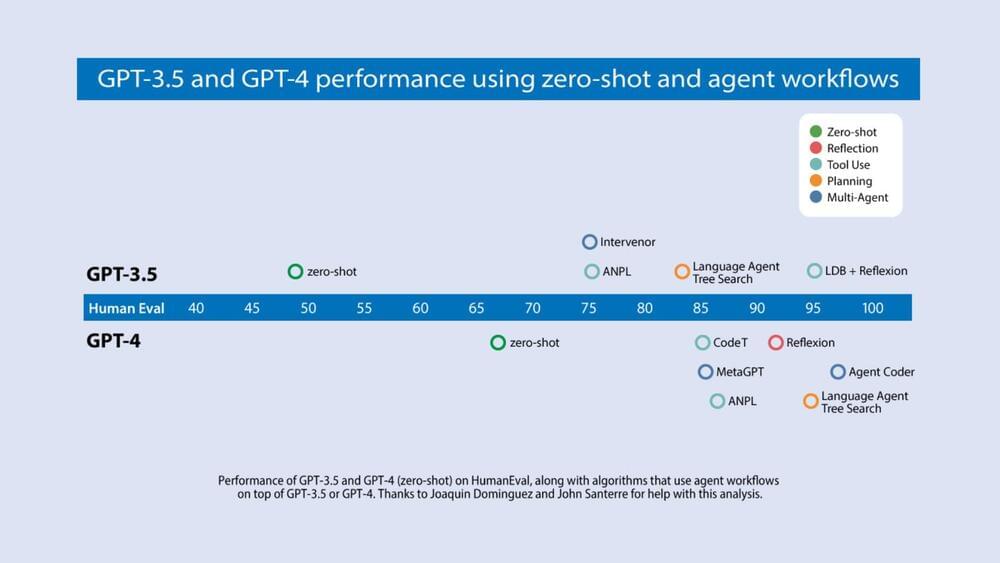
New research exposes vulnerability in HTTP/2 protocol! The CONTINUATION frame can be exploited for DoS attacks, warns security expert Bartek Nowotarsk.


The software development sector stands at the dawn of a transformation powered by artificial intelligence (AI), where AI agents perform development tasks. This transformation is not just about incremental enhancements but a radical reimagining of how software engineering tasks are approached, executed, and delivered. Central to this shift is introducing AI-driven frameworks that transcend traditional code assistance tools, marking a leap toward more autonomous, efficient, and secure software development methodologies.
The integration of AI in software development has been confined largely to providing code suggestions and aiding in file manipulation. This approach, while beneficial, barely scratches the surface of what is technologically feasible. AI-powered tools operate within a constrained scope, missing out on Integrated Development Environments (IDEs)’ vast capabilities, such as comprehensive code building, testing, and version control operations. This limitation underscores a critical gap in the software development toolkit, where the potential for AI to contribute more profoundly to the development lifecycle remains largely untapped.
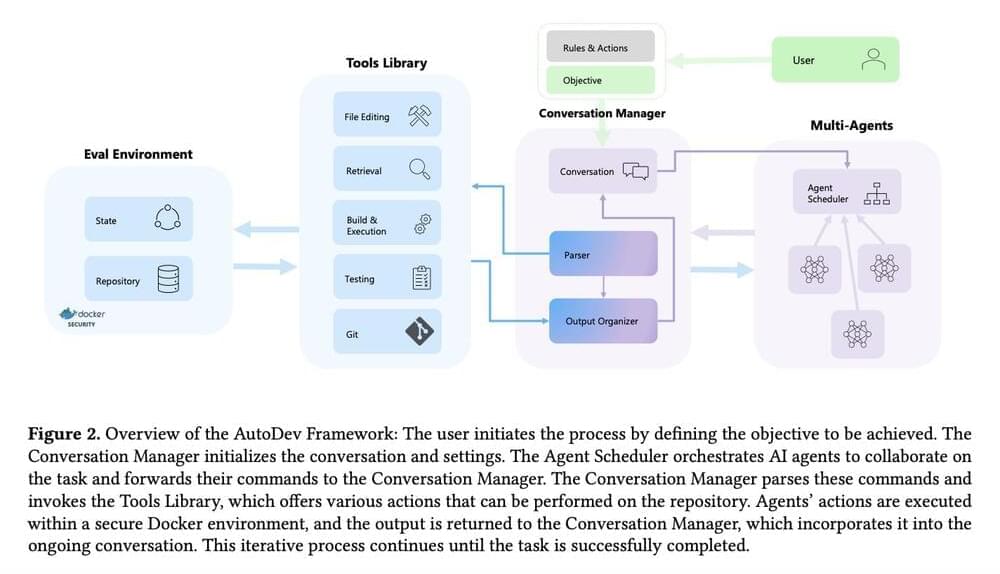
Microsoft researchers present AutoDev, which empowers AI agents to tackle a broad spectrum of software engineering tasks autonomously, from intricate code editing and comprehensive testing to advanced git operations. This framework is designed to focus on autonomy, efficiency, and security. By housing operations within Docker containers, AutoDev ensures that development processes are streamlined and secure, safeguarding user privacy and project integrity through meticulously designed guardrails.
In this episode, Peter and Will dive into satellite technology, what it takes to create a company like Planet, and its effect on ecosystems across the world.
Will Marshall, Chairman, Co-Founder, and CEO of Planet, transitioned from a scientist at NASA to an entrepreneur, leading the company from its inception in a garage to a public entity with over 800 staff. With a background in physics and extensive experience in space technology, he has been instrumental in steering Planet towards its mission of propelling humanity towards sustainability and security, as outlined in its Public Benefit Corporation charter. Recognized for his contributions to the field, Marshall serves on the board of the Open Lunar Foundation and was honored as a Young Global Leader by the World Economic Forum.
Learn more about Planet: https://www.planet.com/
———-
This episode is supported by exceptional companies:
Get started with Fountain Life and become the CEO of your health: https://fountainlife.com/peter/
Multiple Australian projects are on the cutting edge of neurotech breakthroughs and man-machine interfaces – raising questions of security and privacy for human minds.

On Saturday, Chinese scholars unveiled a preliminary proposal draft in Beijing that could potentially shape the nation’s forthcoming artificial intelligence (AI) law.
The proposal draft pays attention to the development issues of industrial practice in the three areas of data, computing power and algorithms, Zhao Jingwu, an associate professor from BeiHang University Law School, told the Global Times.
Zhao said that the proposal also introduces the AI insurance system that encourages the intervention of the insurance market through policy incentives, exploring insurance products suitable for the AI industry. In addition, it proposes the enhancement of citizens’ digital literacy, aiming to prevent and control the security risks of the technology from the user end.
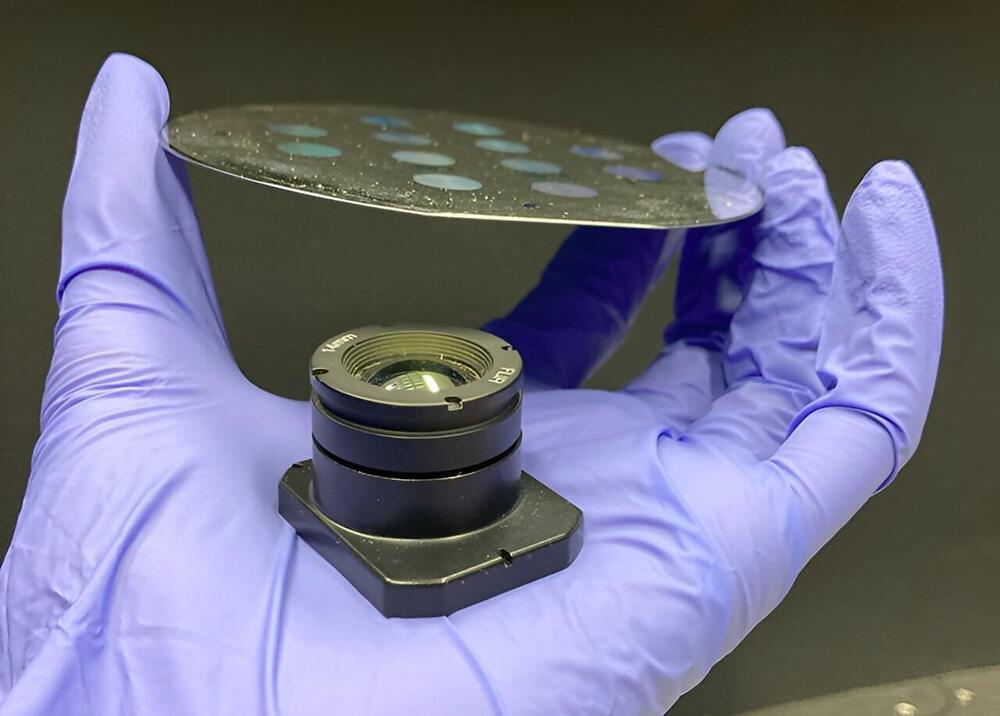
Long-wavelength infrared (LWIR) imaging holds critical significance across many applications, from consumer electronics to defense and national security. It finds applications in night vision, remote sensing, and long-range imaging. However, the conventional refractive lenses employed in these imaging systems are bulky and heavy, which is undesirable for almost all applications. Compounding this issue is the fact that many LWIR refractive lenses are crafted from expensive and limited-supply materials, such as germanium.

The Los Angeles Police Department is warning residents that burglars are using WiFi jammers to easily disarm “connected” surveillance cameras and alarms that are available for cheap on marketplaces like Amazon.
As LA-based news station KTLA5 reports, tech-savvy burglars have been using WiFi jammers, which are small devices that can confuse and overload wireless devices with traffic, to enter homes without setting off alarms — a worrying demonstration of just how easily affordable home security devices from the likes of Ring and Eufy can be disarmed.
As Tom’s Hardware reported last month, instances of WiFi jammers being used by criminals go back several years. Jammers are not only easily available to purchase online, they’re also pretty cheap and can go for as little as $40.

How will that situation change development teams? A common ratio of developers to testers is three to one. At a big bank with 40,000 software engineers, 10,000 might do security, reliability, and quality control. But the AI effect is like squeezing a balloon so it expands on the other side. The coding productivity jump is offset by a dramatic increase in cycles spent on testing.
How Development Teams Can Get Ahead
For software teams, the pressure is on to adapt. Companies that want to stay ahead of the game should first get a handle on a long-time adversary: toil.

Quantum computers, which can solve several complex problems exponentially faster than classical computers, are expected to improve artificial intelligence (AI) applications deployed in devices like autonomous vehicles; however, just like their predecessors, quantum computers are vulnerable to adversarial attacks.
A team of University of Texas at Dallas researchers and an industry collaborator have developed an approach to give quantum computers an extra layer of protection against such attacks. Their solution, Quantum Noise Injection for Adversarial Defense (QNAD), counteracts the impact of attacks designed to disrupt inference—AI’s ability to make decisions or solve tasks.
The team will present research that demonstrates the method at the IEEE International Symposium on Hardware Oriented Security and Trust held May 6–9 in Washington, D.C.