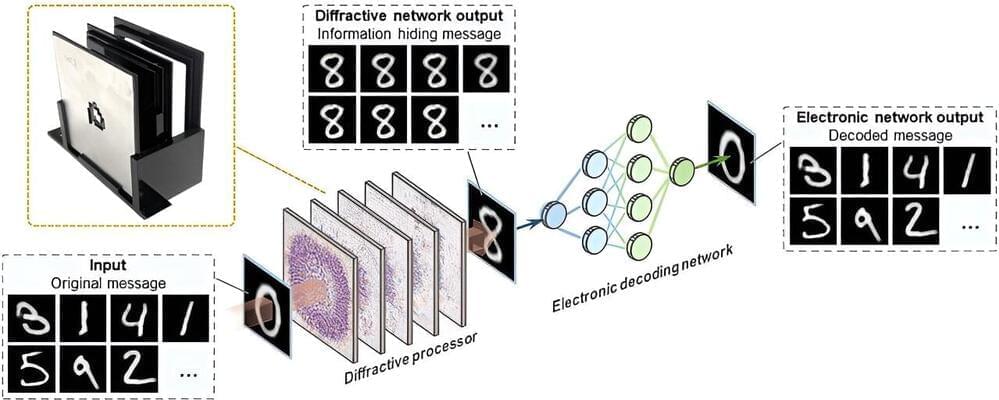
There are plenty of reasons why Google would be interested in going down this route. For example, closer integration would make Android handsets more compatible with Chromebooks. However, it appears the main reason for the move is to accelerate the delivery of AI features.
As the Mountain View-based firm explains, having Chrome OS lean more on Android’s tech stack will make it easier to bring new AI features to Chromebooks. The company adds that along with the change, it wants to maintain the “security, consistent look and feel, and extensive management capabilities” that users are acquainted with.
Google is working on the updates starting today, but notes that users won’t see the changes for a while. The tech giant claims that when everything is ready, the transition will be seamless.