Discover how to secure browser usage in enterprises, from GenAI risks to control enforcement, with a three-stage maturity model.


A new study of integrated development environments (IDEs) like Microsoft Visual Studio Code, Visual Studio, IntelliJ IDEA, and Cursor has revealed weaknesses in how they handle the extension verification process, ultimately enabling attackers to execute malicious code on developer machines.
“We discovered that flawed verification checks in Visual Studio Code allow publishers to add functionality to extensions while maintaining the verified icon,” OX Security researchers Nir Zadok and Moshe Siman Tov Bustan said in a report shared with The Hacker News. “This results in the potential for malicious extensions to appear verified and approved, creating a false sense of trust.”
Specifically, the analysis found that Visual Studio Code sends an HTTP POST request to the domain “marketplace.visualstudio[.]com” to determine if an extension is verified or otherwise.

AT&T has launched a new security feature called “Wireless Lock” that protects customers from SIM swapping attacks by preventing changes to their account information and the porting of phone numbers while the feature is enabled.
This new feature has been available for some customers for almost a year and has now been rolled out to all AT&T customers.
SIM swap attacks are when cybercriminals port, or move, a targeted phone number to a device under their control. This allows them to intercept the target’s calls, texts, and multi-factor authentication codes to breach further accounts, such as email, banking, and cryptocurrency wallets.


The Canadian government has ordered Hikvision’s subsidiary in the country to cease all operations following a review that determined them to pose a national security risk.
The order was forwarded to Hikvision last Friday, and the matter was made public over the weekend by Mélanie Joly, Canada’s Minister of Innovation, Science and Industry.
“Following a National Security Review under the Investment Canada Act, the Government of Canada has ordered Hikvision Canada Inc. to cease all operations in Canada and close its Canadian business,” reads the announcement.

Microsoft has confirmed a new known issue causing delivery delays for June 2025 Windows security updates due to an incorrect metadata timestamp.
As Redmond explains in recent advisory updates, this bug affects Windows 10 and Windows 11 systems in environments with quality update deferral policies that enable admins to delay update installation on managed devices.
While update deployment delays are an expected result when using such policies, the wrong timestamp for the June security updates will postpone them beyond the period specified by administrators, potentially exposing unpatched systems to attacks.
A Los Alamos collaboration has replicated an important but largely forgotten physics experiment: the first deuterium-tritium (DT) fusion observation. As described in the article published in Physical Review C, the reworking of the previously unheralded experiment confirmed the role of University of Michigan physicist Arthur Ruhlig, whose 1938 experiment and observation of deuterium-tritium fusion likely planted the seed for a physics process that informs national security work and nuclear energy research to this day.
“As we’ve uncovered, Ruhlig’s contribution was to hypothesize that DT fusion happens with very high probability when deuterium and tritium are brought sufficiently close together,” said Mark Chadwick, associate Laboratory director for Science, Computation and Theory at Los Alamos. “Replicating his experiment helped us interpret his work and better understand his role, and what proved to be his essentially correct conclusions. The course of nuclear fuel physics has borne out the profound consequences of Arthur Ruhlig’s clever insight.”
The DT fusion reaction is central to enabling fusion technologies, whether as part of the nation’s nuclear deterrence capabilities or in ongoing efforts to develop fusion for civilian energy. For instance, the deuterium-tritium reaction is at the center of efforts at the National Ignition Facility to harness fusion. Los Alamos physicists developed a theory about where the idea came from—Ruhlig—and then built an experiment that would confirm the import and accuracy of Ruhlig’s suggestion.
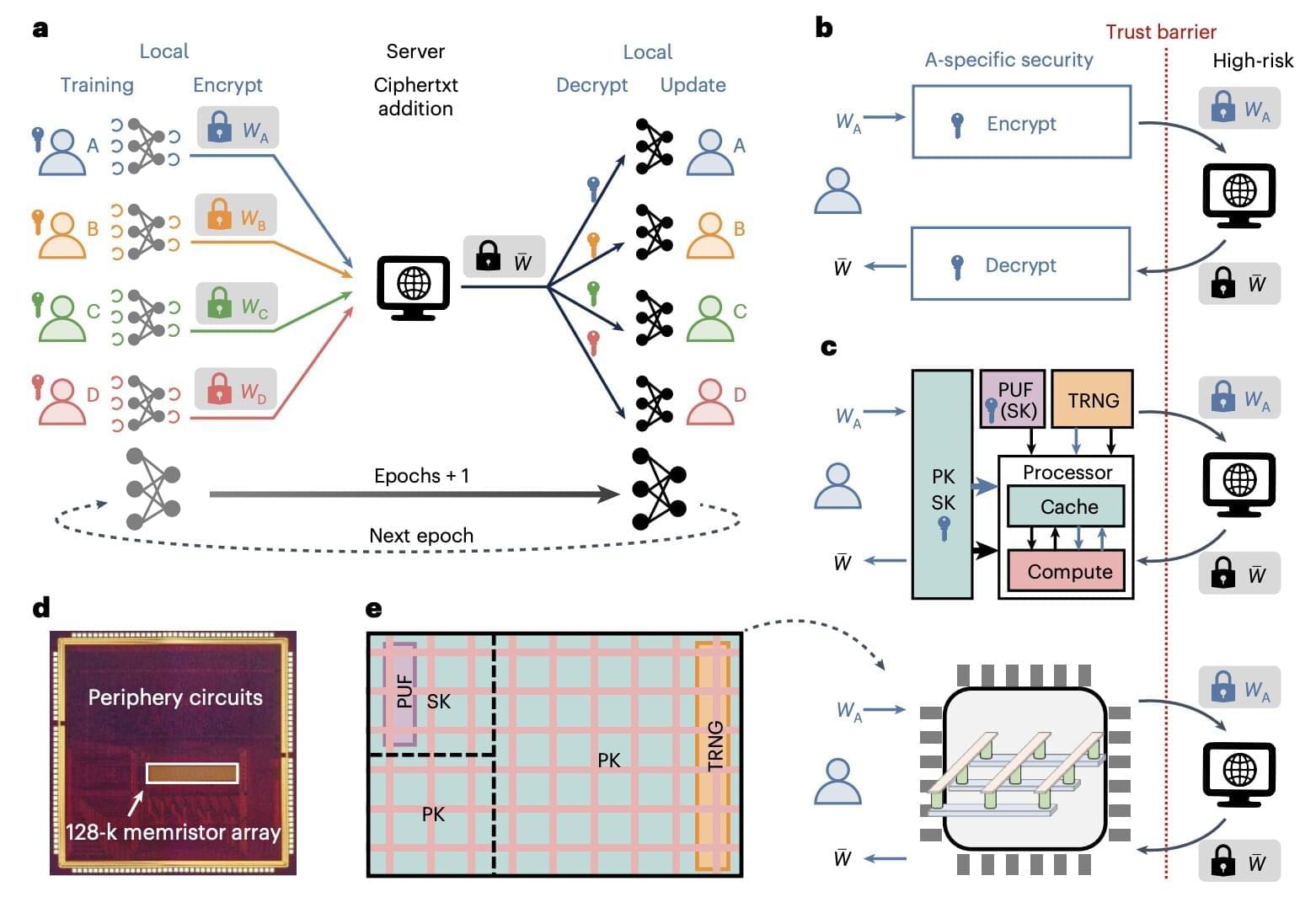
In recent decades, computer scientists have been developing increasingly advanced machine learning techniques that can learn to predict specific patterns or effectively complete tasks by analyzing large amounts of data. Yet some studies have highlighted the vulnerabilities of some AI-based tools, demonstrating that the sensitive information they are fed could be potentially accessed by malicious third parties.
A machine learning approach that could provide greater data privacy is federated learning, which entails the collaborative training of a shared neural network by various users or parties that are not required to exchange any raw data with each other. This technique could be particularly advantageous when applied in sectors that can benefit from AI but that are known to store highly sensitive user data, such as health care and finance.
Researchers at Tsinghua University, the China Mobile Research Institute, and Hebei University recently developed a new compute-in-memory chip for federated learning, which is based on memristors, non-volatile electronic components that can both perform computations and store information, by adapting their resistance based on the electrical current that flowed through them in the past. Their proposed chip, outlined in a paper published in Nature Electronics, was found to boost both the efficiency and security of federated learning approaches.
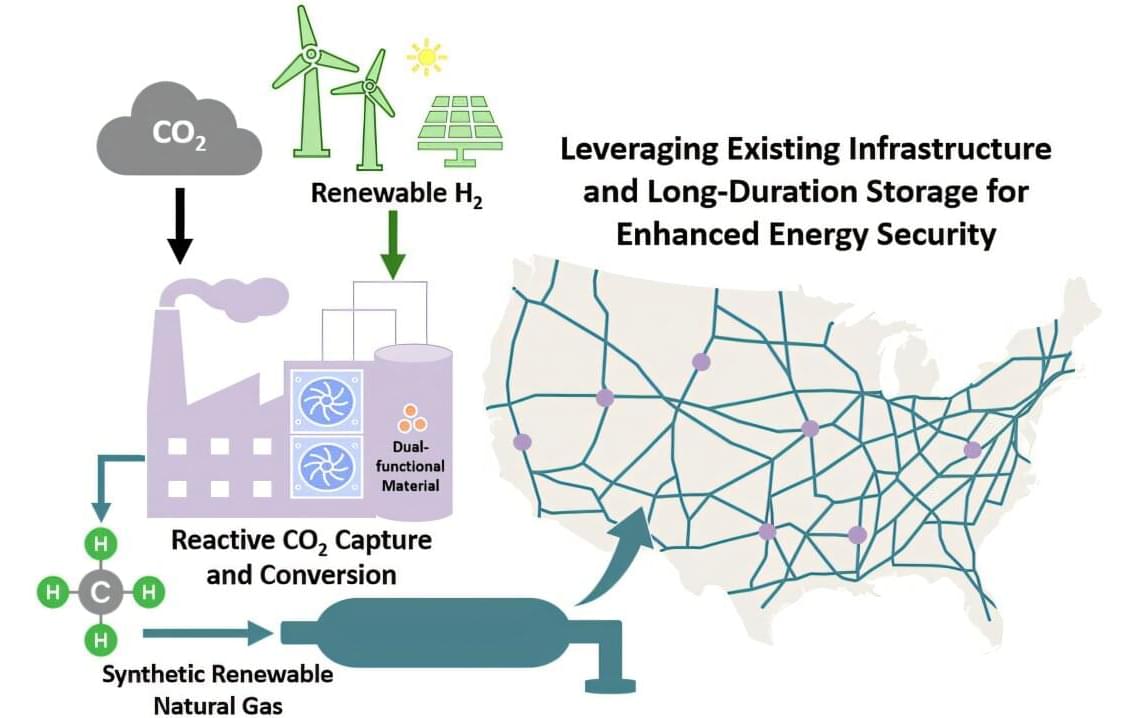
Solar and wind energy are highly variable, dependent on the day, weather and location of the facilities. At times, they can generate more electricity than is needed, but they can also fall short when demand is at its peak. Unfortunately, any extra energy created by these sources is often wasted, as there are few methods that adequately store it long-term. To improve energy security in the United States, the nation requires both sources of energy and novel ways to store and distribute it.
In a new study, published in Cell Reports Sustainability, researchers from Lawrence Livermore National Laboratory (LLNL) have explored how a reactive carbon dioxide capture and conversion (RCC) process could be used to produce synthetic renewable natural gas—a chemical form of long-duration energy storage.
“Rather than sourcing carbon from below-ground, RCC enables the use of above-ground carbon as a resource,” said LLNL scientist and lead author Alvina Aui. “Synthetic renewable natural gas, when used as an energy-storage option, can reduce grid instability caused by the intermittency of energy sources like wind and solar.”