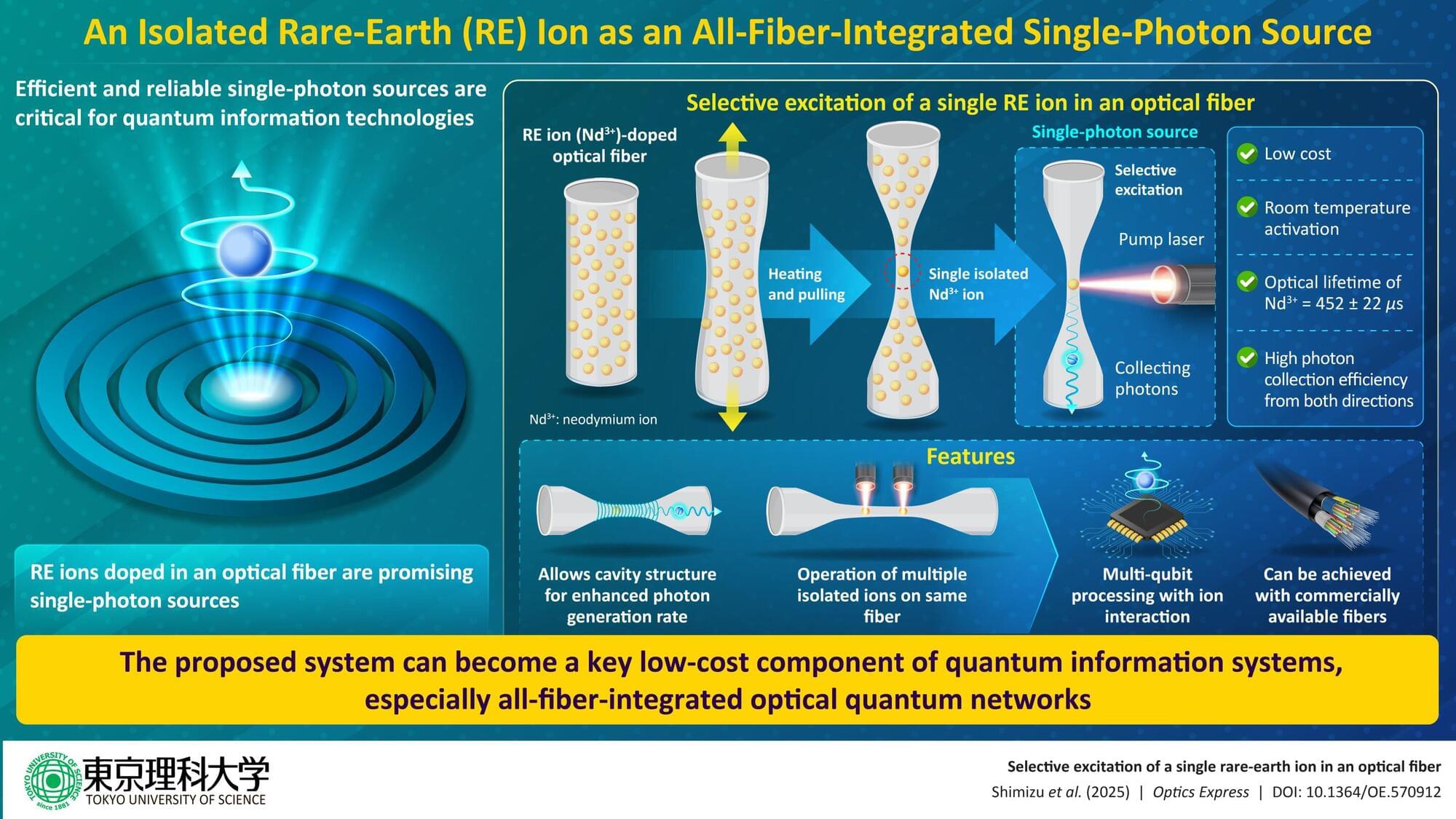
With the rise of quantum computers, the security of our existing communication systems is at risk. Quantum computers will be able to break many of the encryption methods used in current communication systems. To counter this, scientists are developing quantum communication systems, which utilize quantum mechanics to offer stronger security. A crucial building block of these systems is a single-photon source: a device that generates only one light particle at a time.
These photons, carrying quantum information, are then sent through optical fibers. For quantum communication systems to work, it is essential that single photons are injected into optical fibers with extremely low loss.
In conventional systems, single-photon emitters, like quantum dots and rare-earth (RE) element ions, are placed outside the fiber. These photons then must be guided to enter the fiber. However, not all photons make it into the fibers, causing high transmission loss. For practical quantum communication systems, it is necessary to achieve a high-coupling and channeling efficiency between the optical fiber and the emitter.