Turkey gets Wikipedia back, Mayor Pete loses his cyberguy, and more of the week’s top security news.



Cory Doctorow’s sunglasses are seemingly ordinary. But they are far from it when seen on security footage, where his face is transformed into a glowing white orb.
At his local credit union, bemused tellers spot the curious sight on nearby monitors and sometimes ask, “What’s going on with your head?” said Doctorow, chuckling.
The frames of his sunglasses, from Chicago-based eyewear line Reflectacles, are made of a material that reflects the infrared light found in surveillance cameras and represents a fringe movement of privacy advocates experimenting with clothes, ornate makeup and accessories as a defense against some surveillance technologies.
Homeland Security might soon have a new tool to add to its arsenal.
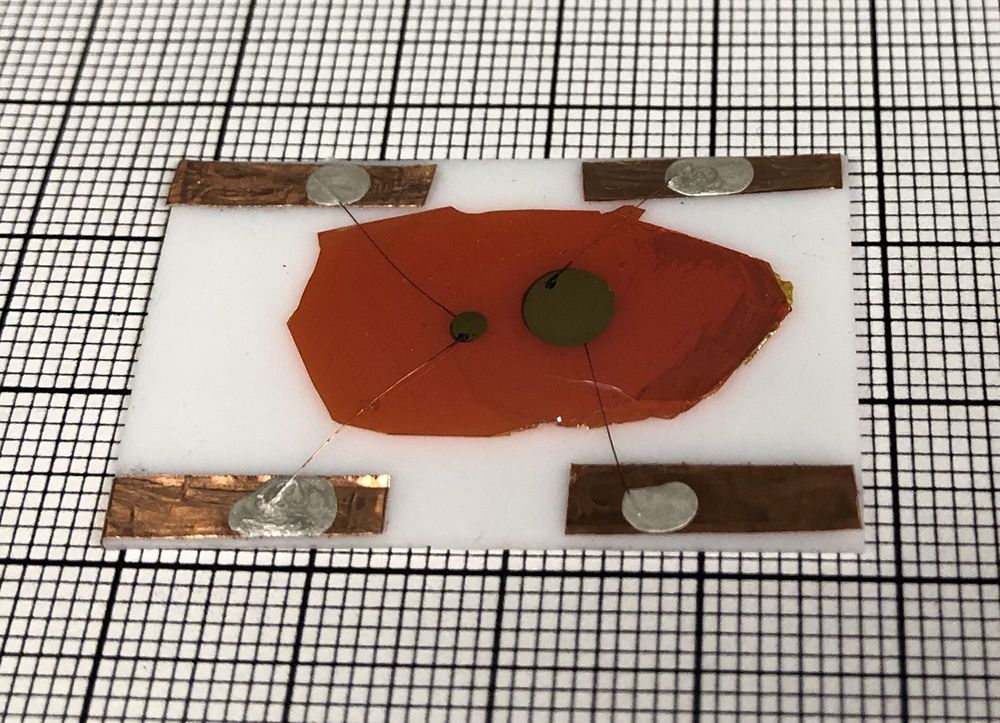
Researchers at Northwestern University and Argonne National Laboratory have developed a new material that opens doors for a new class of neutron detectors.
With the ability to sense smuggled nuclear materials, highly efficient neutron detectors are critical for national security. Currently, there are two classes of detectors which either use helium gas or flashes of light. These detectors are very large—sometimes the size of a wall.

Location: Manhattan, KS

The National Bio and Agro-Defense Facility (NBAF) will be a state-of-the-art biocontainment laboratory for the study of diseases that threaten both America’s animal agricultural industry and public health. DHS S&T is building the facility to standards that fulfill the mission needs of the U.S. Department of Agriculture (USDA) which will own, manage and operate (PDF, 16 pgs., 165 KB) the NBAF once construction and commissioning activities are complete. The NBAF will strengthen our nation’s ability to conduct research, develop vaccines, diagnose emerging diseases, and train veterinarians. DHS S&T will leverage the facility as a national asset to fulfill homeland security mission needs.
The United States currently does not have a laboratory facility with maximum biocontainment (BSL-4) space to study high-consequence zoonotic diseases affecting large livestock. The NBAF will be the first laboratory facility in the U.S. to provide BSL-4 laboratories capable of housing cattle and other large livestock. The NBAF will also feature a vaccine development module. For more information about the facility and intended use of its state-of-the-art features, please visit the USDA NBAF Program website.

Found this article being passed around amongst some of the Colorado/Nebraska drone sightings speculators…
TOPEKA, Kan. (KSNT) – All committee meetings were canceled Tuesday afternoon and all Kansas House members were called to the Kansas Air National Guard for a meeting with the U.S. Department of Homeland Security.
Kansas Deputy Attorney General Jay Scott Emler sent a letter to Speaker Ron Ryckman Tuesday saying that the DHS briefing should be given in a closed caucus.
In the letter, Emler also said the closed session will include information applicable to the security of the State and its citizens.


One of the new products unveiled at CES this year is a new kind of home security system — one that includes drones to patrol your property, along with sensors designed to mimic garden light and a central processor to bring it all together.
Sunflower Labs debuted their new Sunflower Home Awareness System, which includes the eponymous Sunflowers (motion and vibration sensors that look like simple garden lights but can populate a map to show you cars, people and animals on or near your property in real time); the Bee (a fully autonomous drone that deploys and flies on its own, with cameras on board to live-stream video); and the Hive (a charging station for the Bee, which also houses the brains of the operation for crunching all the data gathered by the component parts).
Roving aerial robots keeping tabs on your property might seem a tad dystopian, and perhaps even unnecessary, when you could maybe equip your estate with multiple fixed cameras and sensors for less money and with less complexity. But Sunflower Labs thinks its security system is an evolution of more standard fare because it “learns and reacts to its surroundings,” improving over time.

Mozilla has warned Firefox users to update their browser to the latest version after security researchers found a vulnerability that hackers were actively exploiting in “targeted attacks” against users.
The vulnerability, found by Chinese security company Qihoo 360, was found in Firefox’s just-in-time compiler. The compiler is tasked with speeding up performance of JavaScript to make websites load faster. But researchers found that the bug could allow malicious JavaScript to run outside of the browser on the host computer.
In practical terms, that means an attacker can quietly break into a victim’s computer by tricking the victim into accessing a website running malicious JavaScript code.

The Trump administration is proposing new rules to guide future federal regulation of artificial intelligence used in medicine, transportation and other industries.
But the vagueness of the principles announced by the White House is unlikely to satisfy AI watchdogs who have warned of a lack of accountability as computer systems are deployed to take on human roles in high-risk social settings, such as mortgage lending or job recruitment.
The White House said that in deciding regulatory action, U.S. agencies “must consider fairness, non-discrimination, openness, transparency, safety, and security.” But federal agencies must also avoid setting up restrictions that “needlessly hamper AI innovation and growth,” reads a memo being sent to U.S. agency chiefs from Russell Vought, acting director of the Office of Management and Budget.

The Federal Aviation Administration put forward a rule Thursday that would empower the government to track most drones in the U.S.
The rule will require drones to implement a remote ID system, which will make it possible for third parties to track them. The measure will help law enforcement identify unauthorized drones that may pose a security threat, paving the way for wider adoption of commercial drone technology.
The rule said that the FAA expects all eligible drones in the U.S. to comply with the rule within three years.