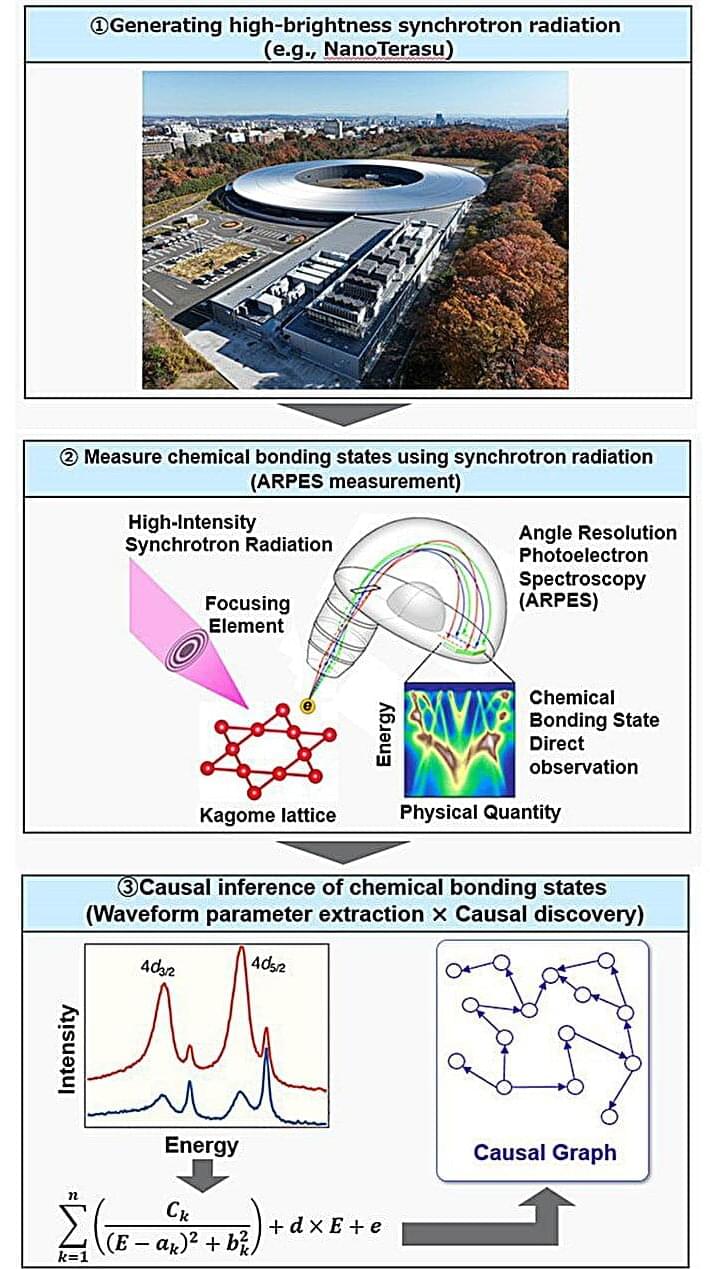
Tohoku University and Fujitsu Limited have successfully used AI to derive new insights into the superconductivity mechanism of a new superconducting material.
Their findings demonstrate an important use case for AI technology in new materials development and suggest that the technology has the potential to accelerate research and development. This could drive innovation in various industries such as the environment and energy, drug discovery and health care, and electronic devices.
The AI technology was used to automatically clarify causal relationships from measurement data obtained at NanoTerasu Synchrotron Light Source. This achievement was published in Scientific Reports.