Brain-computer interfaces may have a profound effect on people with limited mobility or other disabilities, but experts say they also introduce privacy issues that must be mitigated.


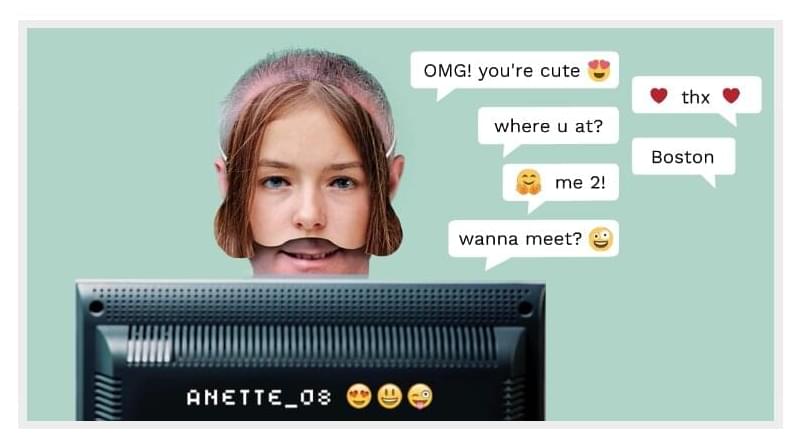
Millions of children log into chat rooms every day to talk with other children. One of these “children” could well be a man pretending to be a 12-year-old girl with far more sinister intentions than having a chat about “My Little Pony” episodes.
Inventor and NTNU professor Patrick Bours at AiBA is working to prevent just this type of predatory behavior. AiBA, an AI-digital moderator that Bours helped found, can offer a tool based on behavioral biometrics and algorithms that detect sexual abusers in online chats with children.
And now, as recently reported by Dagens Næringsliv, a national financial newspaper, the company has raised capital of NOK 7.5. million, with investors including Firda and Wiski Capital, two Norwegian-based firms.

View insights.
In a paper distributed via ArXiv, titled “Exploring the Unprecedented Privacy Risks of the Metaverse,” boffins at UC Berkeley in the US and the Technical University of Munich in Germany play-tested an “escape room” virtual reality (VR) game to better understand just how much data a potential attacker could access. Through a 30-person study of VR usage, the researchers – Vivek Nair (UCB), Gonzalo Munilla Garrido (TUM), and Dawn Song (UCB) – created a framework for assessing and analyzing potential privacy threats. They identified more than 25 examples of private data attributes available to potential attackers, some of which would be difficult or impossible to obtain from traditional mobile or web applications. The metaverse that is rapidly becoming a part of our world has long been an essential part of the gaming community. Interaction-based games like Second Life, Pokemon Go, and Minecraft have existed as virtual social interaction platforms. The founder of Second Life, Philip Rosedale, and many other security experts have lately been vocal about Meta’s impact on data privacy. Since the core concept is similar, it is possible to determine the potential data privacy issues apparently within Meta.
There has been a buzz going around the tech market that by the end of 2022, the metaverse can revive the AR/VR device shipments and take it as high as 14.19 million units, compared to 9.86 million in 2021, indicating a year-over-year increase of about 35% to 36%. The AR/VR device market will witness an enormous boom in the market due to component shortages and the difficulty to develop new technologies. The growth momentum will also be driven by the increased demand for remote interactivity stemming from the pandemic. But what will happen when these VR or metaverse headsets start stealing your precious data? Not just headsets but smart glasses too are prime suspect when it comes to privacy concerns.
Several weeks ago, Facebook introduced a new line of smart glasses called Ray-Ban Stories, which can take photos, shoot 30-second videos, and post them on the owner’s Facebook feed. Priced at US$299 and powered by Facebook’s virtual assistant, the web-connected shades can also take phone calls and play music or podcasts.
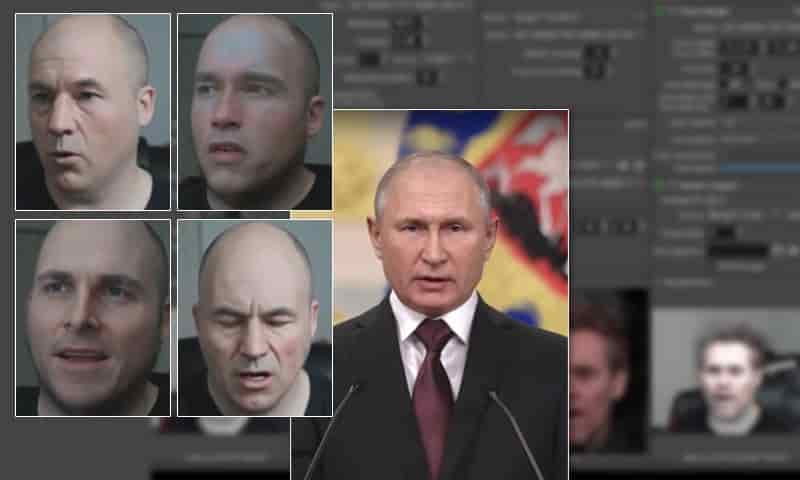
A new collaboration between a researcher from the United States’ National Security Agency (NSA) and the University of California at Berkeley offers a novel method for detecting deepfake content in a live video context – by observing the effect of monitor lighting on the appearance of the person at the other end of the video call.

In November last year, an undercover agent with the FBI was inside a group on Amazon-owned messaging app Wickr, with a name referencing young girls. The group was devoted to sharing child sexual abuse material (CSAM) within the protection of the encrypted app, which is also used by the U.S. government, journalists and activists for private communications. Encryption makes it almost impossible for law enforcement to intercept messages sent over Wickr, but this agent had found a way to infiltrate the chat, where they could start piecing together who was sharing the material.
As part of the investigation into the members of this Wickr group, the FBI used a previously unreported search warrant method to force one member to unlock the encrypted messaging app using his face. The FBI has previously forced users to unlock an iPhone with Face ID, but this search warrant, obtained by Forbes, represents the first known public record of a U.S. law enforcement agency getting a judge’s permission to unlock an encrypted messaging app with someone’s biometrics.
According to the warrant, the FBI first tracked down the suspect by sending a request for information, via an unnamed foreign law enforcement partner, to the cloud storage provider hosting the illegal images. That gave them the Gmail address the FBI said belonged to Christopher Terry, a 53-year-old Knoxville, Tennessee resident, who had prior convictions for possession of child exploitation material. It also provided IP addresses used to create the links to the CSAM. From there, investigators asked Google and Comcast via administrative subpoenas (data requests that don’t have the same level of legal requirements as search warrants) for more identifying information that helped them track down Terry and raid his home.
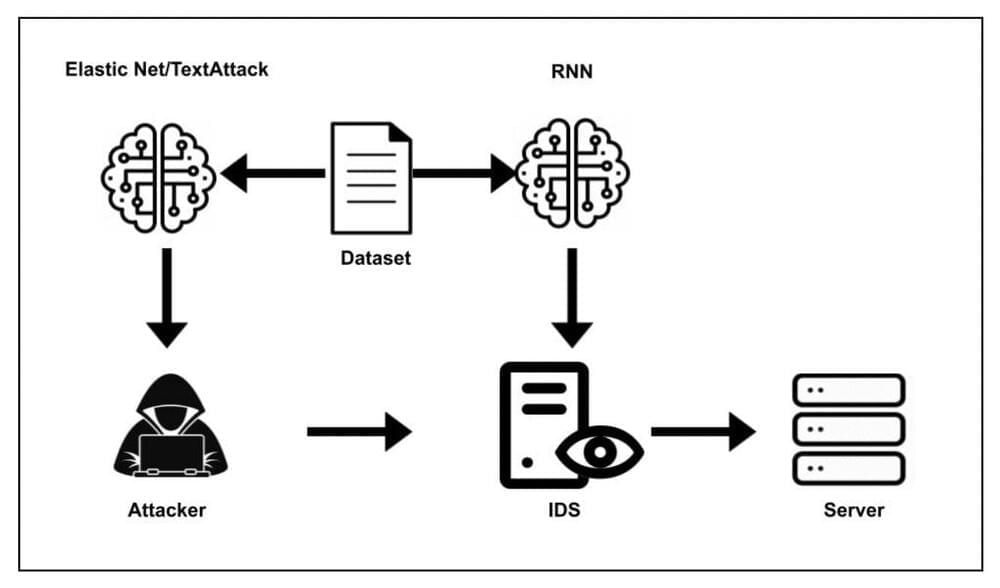
Deep learning techniques have recently proved to be highly promising for detecting cybersecurity attacks and determining their nature. Concurrently, many cybercriminals have been devising new attacks aimed at interfering with the functioning of various deep learning tools, including those for image classification and natural language processing.
Perhaps the most common among these attacks are adversarial attacks, which are designed to “fool” deep learning algorithms using data that has been modified, prompting them to classify it incorrectly. This can lead to the malfunctioning of many applications, biometric systems, and other technologies that operate through deep learning algorithms.
Several past studies have shown the effectiveness of different adversarial attacks in prompting deep neural networks (DNNs) to make unreliable and false predictions. These attacks include the Carlini & Wagner attack, the Deepfool attack, the fast gradient sign method (FGSM) and the Elastic-Net attack (ENA).

An artificial nose, which is combined with machine learning and built with a 16-channel sensor array was found to be able to authenticate up to 20 individuals with an average accuracy of more than 97%.
“These techniques rely on the physical uniqueness of each individual, but they are not foolproof. Physical characteristics can be copied, or even compromised by injury,” explains Chaiyanut Jirayupat, first author of the study. “Recently, human scent has been emerging as a new class of biometric authentication, essentially using your unique chemical composition to confirm who you are.”
The team turned to see if human breath could be used after finding that the skin does not produce a high enough concentration of volatile compounds for machines to detect.

Biometric authentication like fingerprint and iris scans are a staple of any spy movie, and trying to circumvent those security measures is often a core plot point. But these days the technology is not limited to spies, as fingerprint verification and facial recognition are now common features on many of our phones.
Now, researchers have developed a new potential odorous option for the biometric security toolkit: your breath. In a report published in Chemical Communications, researchers from Kyushu University’s Institute for Materials Chemistry and Engineering, in collaboration with the University of Tokyo, have developed an olfactory sensor capable of identifying individuals by analyzing the compounds in their breath.
Combined with machine learning, this “artificial nose,” built with a 16-channel sensor array, was able to authenticate up to 20 individuals with an average accuracy of more than 97%.
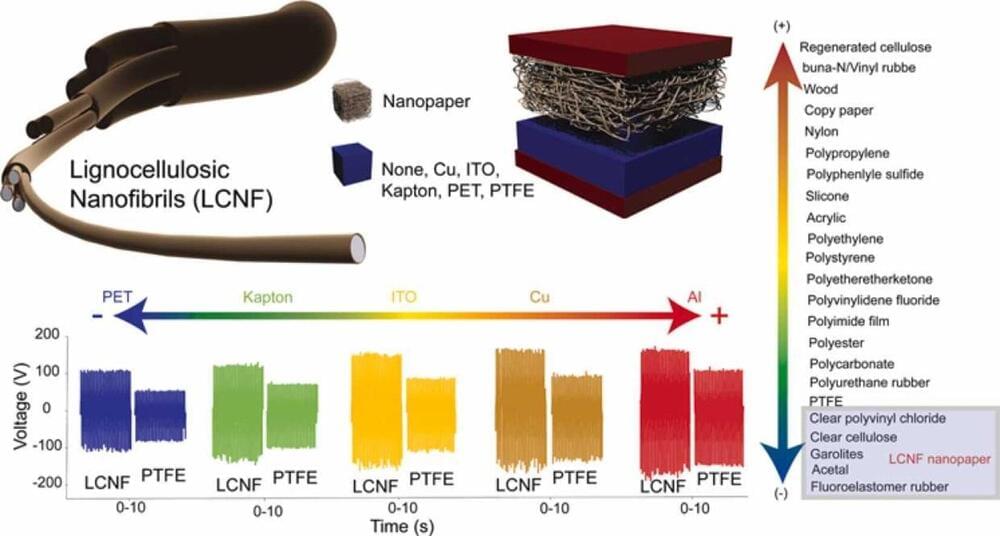
Wood-derived materials can be used to harvest electrical energy from everyday movements such as walking, according to University of Toronto and University of Waterloo researchers.
In a new study recently published in Nano Energy, the team demonstrated the use of lignocellulosic nanofibrils—derived from tree bark —in a prototype self-powered device capable of sending a wireless signal to a smartphone via bluetooth.
Such devices can be used to track biometric data such as heart rate, oxygen levels or skin conductivity. The innovation could improve the performance of these devices while lowering their environmental impact.
Anthony J. Ferrante, Global Head of Cybersecurity and Senior Managing Director, FTI Consulting, Inc.
Artificial intelligence (AI) models are built with a type of machine learning called deep neural networks (DNNs), which are similar to neurons in the human brain. DNNs make the machine capable of mimicking human behaviors like decision making, reasoning and problem solving. This presentation will discuss the security, ethical and privacy concerns surrounding this technology. Learning Objectives:1: Understand that the solution to adversarial AI will come from a combination of technology and policy.2: Learn that coordinated efforts among key stakeholders will help to build a more secure future.3: Learn how to share intelligence information in the cybersecurity community to build strong defenses.