The answer may be counter-intuitive: Not only can Bitcoin be widely adopted under a supply cap, its trust and integrity are a direct result of a provably limited supply. As a result, it will flourish because it is capped.
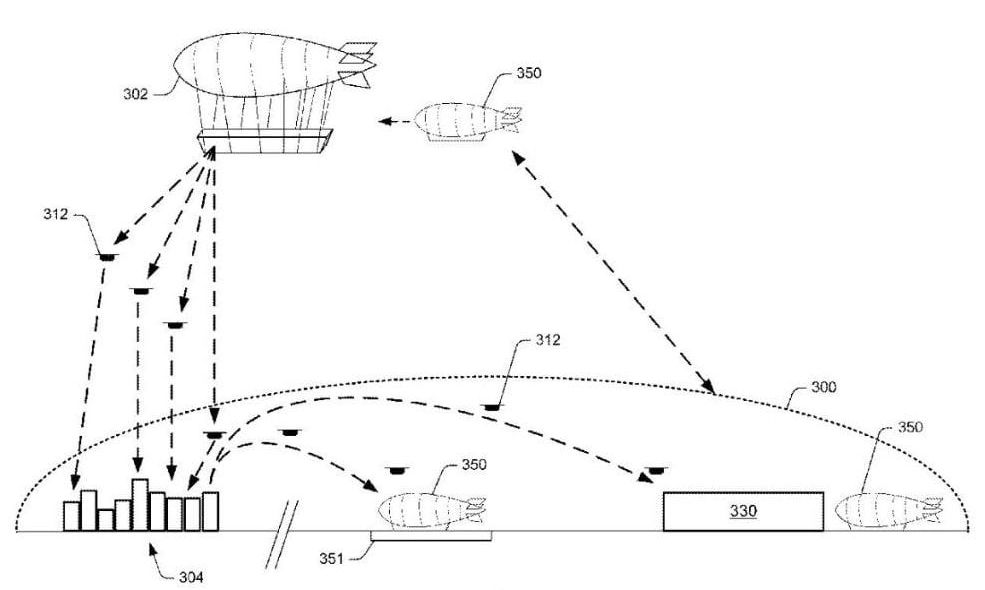
Everyone Can Own and Trade a Limited Commodity, IF…
…if it is both measurable and divisible. Bitcoin has a capped supply just as gold has a capped supply. Although both assets will be mined for some time into the future, there is only so much that will ever be uncovered. Thereafter, the total pie cannot grow.
But the transaction units will continue to grow as needed, because the pie is divisible into very, very tiny units:
There will eventually be 21 million BTC and each coin is divisible into 108 units. This yields (21 million * 100 million), or 21 trillion exchangeable units. And, it can be divided further by consensus.
As Bitcoin is adopted—whether as a simple payment instrument, an investment asset or even as national currencies around the world—each unit of the limited supply simply rises in value. If thought of as a currency, with a value established by supply & demand, it leads to a deflationary economy.
But, Isn’t Deflation Bad for the Economy?
 It’s common to associate deflation with economic ills. One need only glance back at the the last century to conclude that deflation coincides with wars, joblessness, recession and a crippling concentration of wealth. Perhaps, just as bad, the tools used to pull a nation out of deflation often force governments to cherry pick beneficiaries of stimulus spending.
It’s common to associate deflation with economic ills. One need only glance back at the the last century to conclude that deflation coincides with wars, joblessness, recession and a crippling concentration of wealth. Perhaps, just as bad, the tools used to pull a nation out of deflation often force governments to cherry pick beneficiaries of stimulus spending.
But it is important to note that deflation plays no role in causing these things. On the contrary, it is an effect rather than a cause… In fact, when a supply cap is introduced as a designed control input for monetary policy, all sorts of good things follow. I address these in various answers at Quora. Dig in:
Philip Raymond co-chairs Cryptocurrency Standards Association. He was host and producer of The Bitcoin Event in New York. In his spare time, he edits A Wild Duck



 It’s common to associate deflation with economic ills. One need only glance back at the the last century to conclude that deflation coincides with wars, joblessness, recession and a crippling concentration of wealth. Perhaps, just as bad, the tools used to pull a nation out of deflation often force governments to cherry pick beneficiaries of stimulus spending.
It’s common to associate deflation with economic ills. One need only glance back at the the last century to conclude that deflation coincides with wars, joblessness, recession and a crippling concentration of wealth. Perhaps, just as bad, the tools used to pull a nation out of deflation often force governments to cherry pick beneficiaries of stimulus spending.