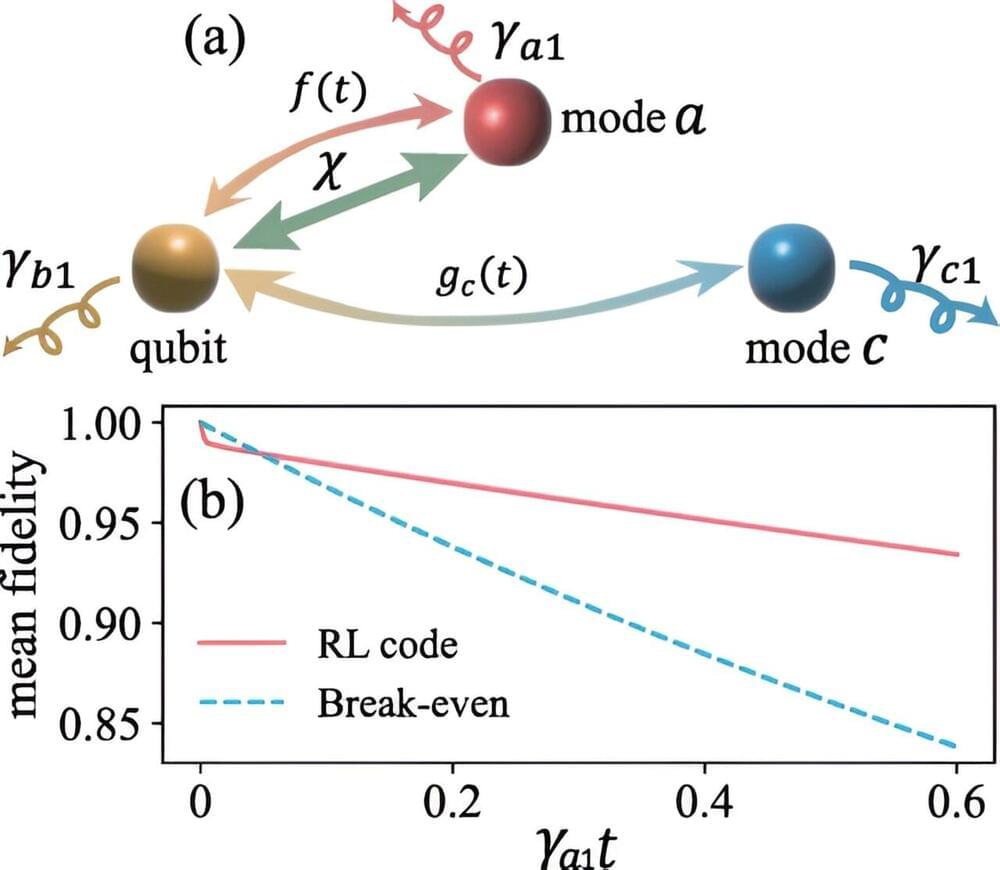
In a new Physical Review Letters study, scientists have successfully presented a proof of concept to demonstrate a randomness-free test for quantum correlations and non-projective measurements, offering a groundbreaking alternative to traditional quantum tests that rely on random inputs.
“Quantum correlation” is a fundamental phenomenon in quantum mechanics and one that is central to quantum applications like communication, cryptography, computing, and information processing.
Bell’s inequality, or Bell’s theory, named after physicist John Stewart Bell, is the standard test used to determine the nature of correlation. However, one of the challenges with using Bell’s theorem is the requirement of seed randomness for selecting measurement settings.