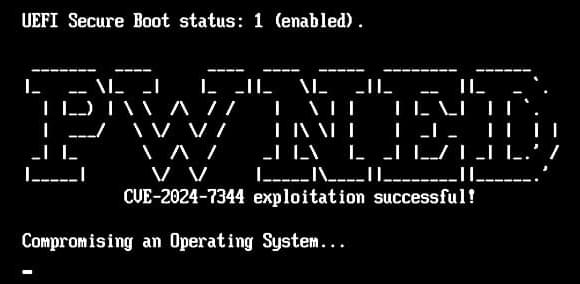
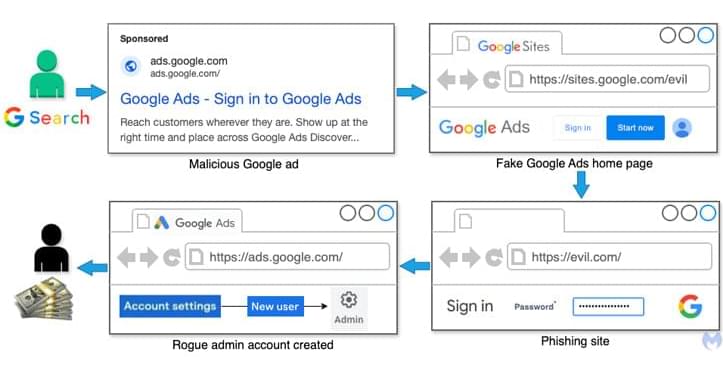
Threat actors on X are exploiting the news around Ross Ulbricht to direct unsuspecting users to a Telegram channel that tricks them into run PowerShell code that infects them with malware.
The attack, spotted by vx-underground, is a new variant of the “Click-Fix” tactic that has become very popular among threat actors to distribute malware over the past year.
However, instead of being fixes for common errors, this variant pretends to be a captcha or verification system that users must run to join the channel.