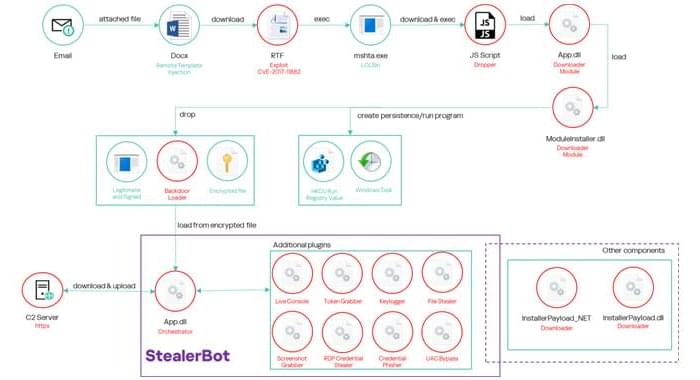
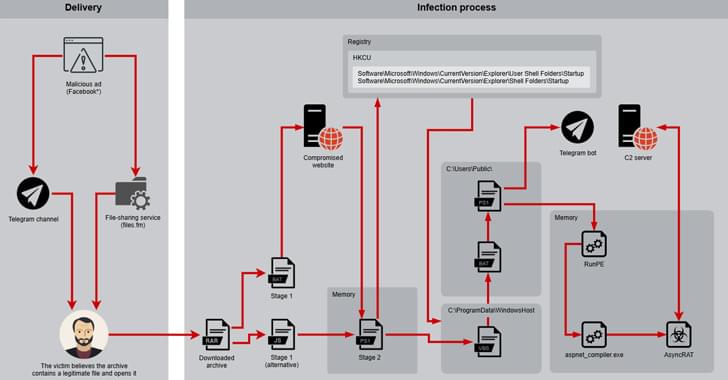
The Black Basta ransomware operation created an automated brute-forcing framework dubbed ‘BRUTED’ to breach edge networking devices like firewalls and VPNs.
The framework has enabled BlackBasta to streamline initial network access and scale ransomware attacks on vulnerable internet-exposed endpoints.
The discovery of BRUTED comes from EclecticIQ researcher Arda Büyükkaya following an in-depth examination of the ransomware gang’s leaked internal chat logs.