New research shows your brain can reshape your gut bacteria in just 2 hours — here’s what it means for stress, immunity, mood, and biohacking



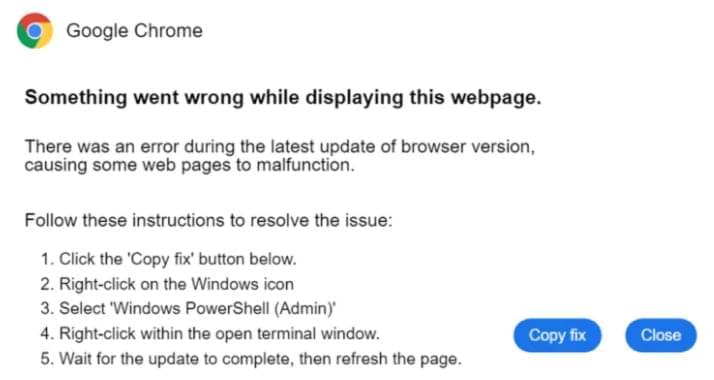

The problem? The file was unencrypted. No password protection. No security. Just a plain text file with millions of sensitive pieces of data.
Based on his analysis, Fowler determined the data was captured by some kind of infostealer malware. A popular tool used by cybercriminals, an infostealer is designed to grab usernames, passwords, and other sensitive data from breached sites and servers. Once the criminals get their hands on the data, they can use it to launch their own attacks or peddle the information on the dark web.
After finding the database, Fowler contacted the hosting provider, which removed it from public access. Since the provider would not disclose the name of the file’s owner, Fowler said he didn’t know if the database was created legitimately and then accidentally exposed or intentionally used for malicious reasons.

By Chuck Brooks
Dear Friends and Colleagues, this issue of the Security & Insights newsletter focuses on cybersecurity and the convergence of devices and networks. The convergence of the Internet of Things, industrial control systems (ICS), operational technology (OT), and information technology (IT) has revealed vulnerabilities and expanded attack surfaces. They are prime targets for hackers, who frequently look for unprotected ports and systems on internet-connected industrial devices. Because they provide several avenues of entry for attackers and because older OT systems were not built to withstand cyberattacks, IT/OT/ICS supply chains in continuous integration (CI) are especially vulnerable. Below is a collection of articles that address the challenges and threats of cybersecurity for connected devices and people.
Thanks for reading and stay safe! Chuck Brooks
Growing cyberthreats to the internet of things.

Cybersecurity researchers are calling attention to a new Linux cryptojacking campaign that’s targeting publicly accessible Redis servers.
The malicious activity has been codenamed RedisRaider by Datadog Security Labs.
“RedisRaider aggressively scans randomized portions of the IPv4 space and uses legitimate Redis configuration commands to execute malicious cron jobs on vulnerable systems,” security researchers Matt Muir and Frederic Baguelin said.

SK Telecom says that a recently disclosed cybersecurity incident in April, first occurred all the way back in 2022, ultimately exposing the USIM data of 27 million subscribers.
SK Telecom is the largest mobile network operator in South Korea, holding roughly half of the national market.
On April 19, 2025, the company detected malware on its networks and responded by isolating the equipment suspected of being hacked.

While the documents refer to the education company only as “Victim-2” and the U.S. attorney’s office declined to name the victim, a person familiar with the matter told NBC News that it is PowerSchool. The hack of PowerSchool last year is believed to be the largest breach of American children’s sensitive data to date.
According to his plea agreement, Lane admitted obtaining information from a protected computer and aggravated identity theft and agreed not to challenge a prison sentence shorter than nine years and four months. He got access simply by trying an employee’s stolen username and password combination, the complaint says, echoing a private third-party assessment of the incident previously reported by NBC News.