Four individuals were arrested in connection with £440M cyber attacks on Marks & Spencer, Co-op, and Harrods, linked to the Scattered Spider group.


Quantum computers have the potential to revolutionize computing by solving complex problems that stump even today’s fastest machines. Scientists are exploring whether quantum computers could one day help streamline global supply chains, create ultra-secure encryption to protect sensitive data against even the most powerful cyberattacks, or even develop more effective drugs by simulating their behavior at the atomic level.
But building efficient quantum computers isn’t just about developing faster chips or better hardware. It also requires a deep understanding of quantum mechanics—the strange rules that govern the tiniest building blocks of our universe, such as atoms and electrons—and how to effectively move information through quantum systems.
In a paper published in Physics Review X, a team of physicists—including graduate student Elizabeth Champion and assistant professor Machiel Blok from the University of Rochester’s Department of Physics and Astronomy—outlined a method to address a tricky problem in quantum computing: how to efficiently move information within a multi-level system using quantum units called qudits.



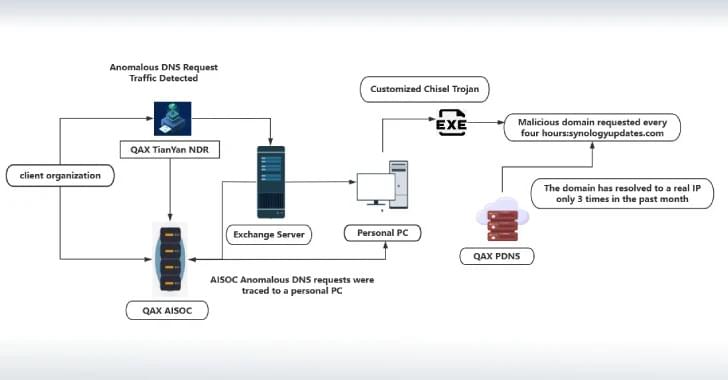
Cybersecurity researchers have shed light on a previously undocumented threat actor called NightEagle (aka APT-Q-95) that has been observed targeting Microsoft Exchange servers as a part of a zero-day exploit chain designed to target government, defense, and technology sectors in China.
According to QiAnXin’s RedDrip Team, the threat actor has been active since 2023 and has switched network infrastructure at an extremely fast rate. The findings were presented at CYDES 2025, the third edition of Malaysia’s National Cyber Defence & Security Exhibition and Conference held between July 1 and 3, 2025.

