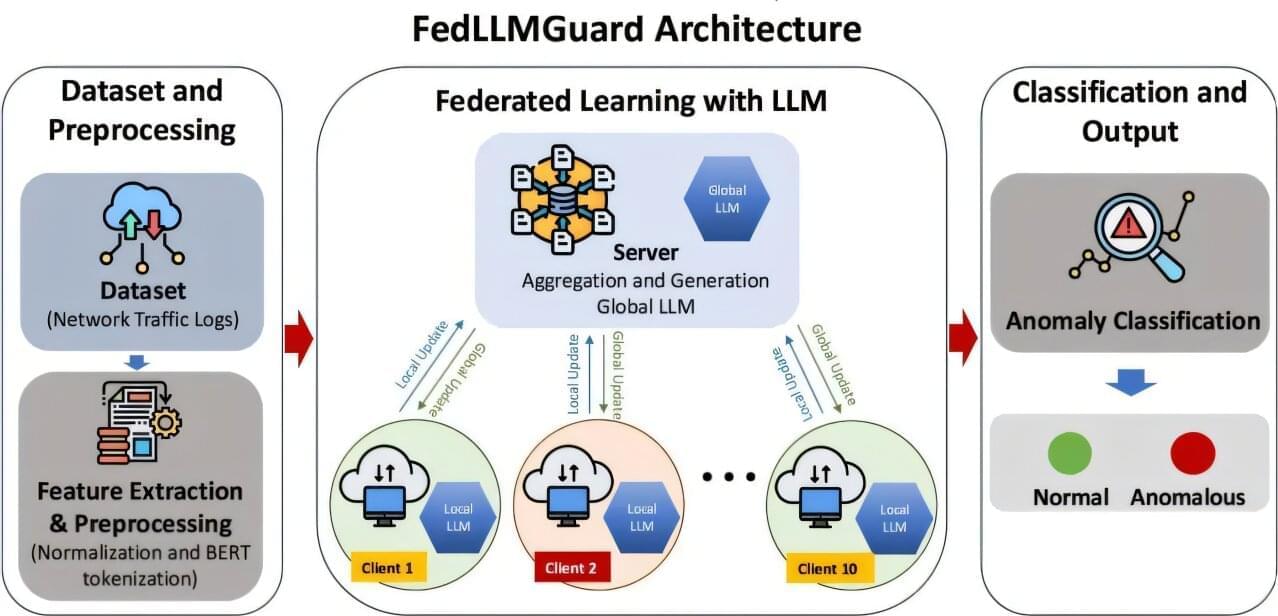
European law enforcement in an operation codenamed ‘SIMCARTEL’ has dismantled an illegal SIM-box service that enabled more than 3,200 fraud cases and caused at least 4.5 million euros in losses.
The cybercriminal online services had about 1,200 SIM-box devices with 40,000 SIM cards to provide phone numbers that were used in telecommunication crimes ranging from phishing and investment fraud to impersonation and extortion.
In an announcement today, Europol says that the cybercrime service operated through two websites, gogetsms.com and apisim.com, which have been seized and now display a law enforcement banner.