The British government isn’t the only one looking to introduce digital ID cards. There is so much to worry about here, not least the threat of hacks, says Annalee Newitz


The British government isn’t the only one looking to introduce digital ID cards. There is so much to worry about here, not least the threat of hacks, says Annalee Newitz

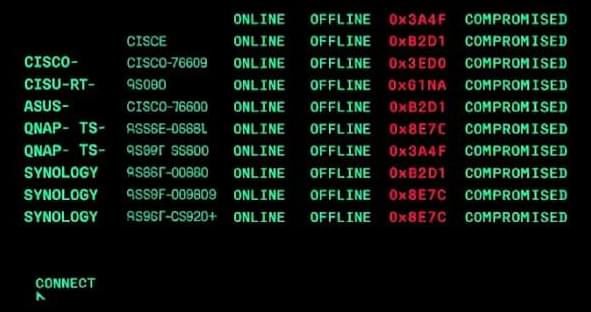
In a report published earlier this week, Fortra said phishing kits associated with the Smishing Triad are being used to increasingly target brokerage accounts to obtain banking credentials and authentication codes, with attacks targeting these accounts witnessing a fivefold jump in the second quarter of 2025 compared to the same period last year.
“Once compromised, attackers manipulate stock market prices using ‘ramp and dump’ tactics,” security researcher Alexis Ober said. “These methods leave almost no paper trail, further heightening the financial risks that arise from this threat.”
The adversarial collective is said to have evolved from a dedicated phishing kit purveyor into a “highly active community” that brings together disparate threat actors, each of whom plays a crucial role in the phishing-as-a-service (PhaaS) ecosystem.
A Pakistan-nexus threat actor has been observed targeting Indian government entities as part of spear-phishing attacks designed to deliver a Golang-based malware known as DeskRAT.
The activity, observed in August and September 2025 by Sekoia, has been attributed to Transparent Tribe (aka APT36), a state-sponsored hacking group known to be active since at least 2013. It also builds upon a prior campaign disclosed by CYFIRMA in August 2025.
The attack chains involve sending phishing emails containing a ZIP file attachment, or in some cases, a link pointing to an archive hosted on legitimate cloud services like Google Drive. Present within the ZIP file is a malicious Desktop file embedding commands to display a decoy PDF (“CDS_Directive_Armed_Forces.pdf”) using Mozilla Firefox while simultaneously executing the main payload.


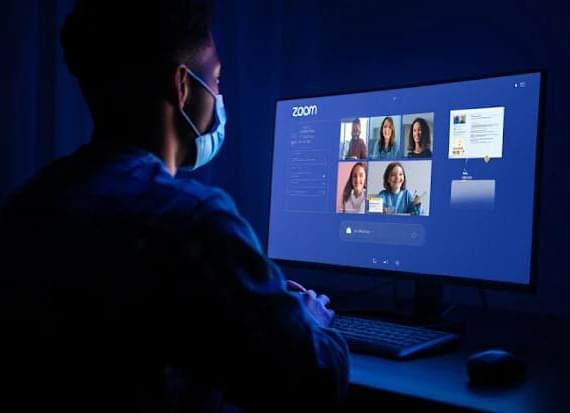
Cybersecurity researchers have disclosed details of a coordinated spear-phishing campaign dubbed PhantomCaptcha targeting organizations associated with Ukraine’s war relief efforts to deliver a remote access trojan that uses a WebSocket for command-and-control (C2).
The activity, which took place on October 8, 2025, targeted individual members of the International Red Cross, Norwegian Refugee Council, United Nations Children’s Fund (UNICEF) Ukraine office, Norwegian Refugee Council, Council of Europe’s Register of Damage for Ukraine, and Ukrainian regional government administrations in the Donetsk, Dnipropetrovsk, Poltava, and Mikolaevsk regions, SentinelOne said in a new report published today.
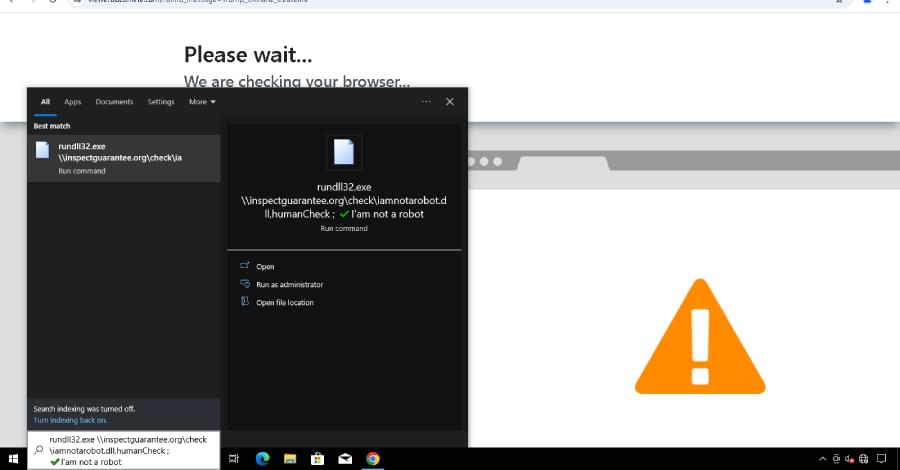
The phishing emails have been found to impersonate the Ukrainian President’s Office, carrying a booby-trapped PDF document that contains an embedded link, which, when clicked, redirects victims to a fake Zoom site (“zoomconference[.]app”) and tricks them into running a malicious PowerShell command via a ClickFix-style fake Cloudflare CAPTCHA page under the guise of a browser check.

CVE-2025–53770, assessed to be a patch bypass for CVE-2025–49704 and CVE-2025–49706, has been weaponized as a zero-day by three Chinese threat groups, including Linen Typhoon (aka Budworm), Violet Typhoon (aka Sheathminer), and Storm-2603, the latter of which is linked to the deployment of Warlock, LockBit, and Babuk ransomware families in recent months.
However, the latest findings from Symantec indicate that a much wider range of Chinese threat actors have abused the vulnerability. This includes the Salt Typhoon (aka Glowworm) hacking group, which is said to have leveraged the ToolShell flaw to deploy tools like Zingdoor, ShadowPad, and KrustyLoader against the telecom entity and the two government bodies in Africa.
KrustyLoader, first detailed by Synacktiv in January 2024, is a Rust-based loader previously put to use by a China-nexus espionage group dubbed UNC5221 in attacks exploiting flaws in Ivanti Endpoint Manager Mobile (EPMM) and SAP NetWeaver.