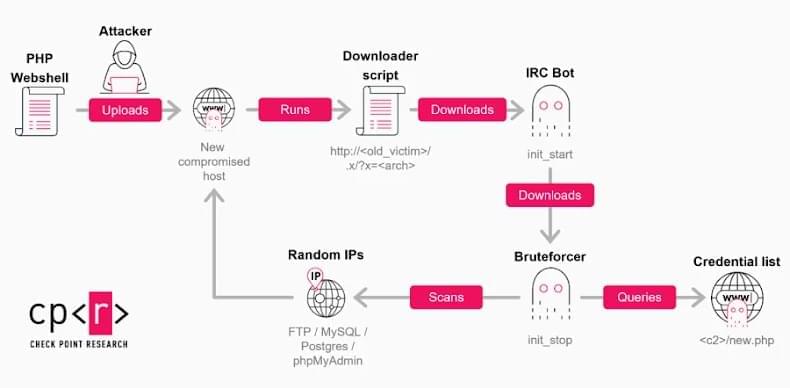
A newly discovered advanced cloud-native Linux malware framework named VoidLink focuses on cloud environments, providing attackers with custom loaders, implants, rootkits, and plugins designed for modern infrastructures.
VoidLink is written in Zig, Go, and C, and its code shows signs of a project under active development, with extensive documentation, and likely intended for commercial purposes.
Malware analysts at cybersecurity company Check Point say that VoidLink can determine if it runs inside Kubernetes or Docker environments and adjust its behavior accordingly.