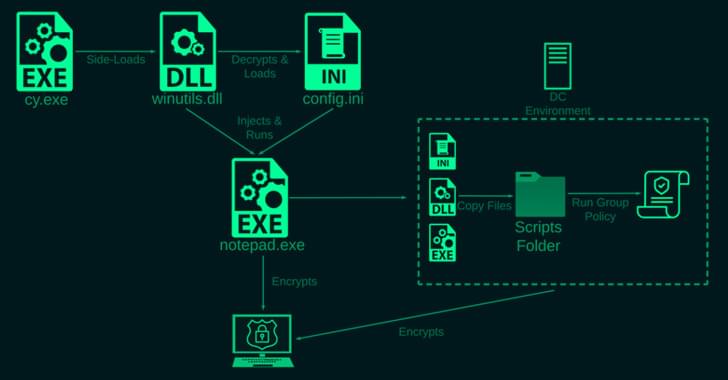
Cybersecurity researchers have taken the wraps off a previously undocumented ransomware strain called Rorschach that’s both sophisticated and fast.
“What makes Rorschach stand out from other ransomware strains is its high level of customization and its technically unique features that have not been seen before in ransomware,” Check Point Research said in a new report. “In fact, Rorschach is one of the fastest ransomware strains ever observed, in terms of the speed of its encryption.”
The cybersecurity firm said it observed the ransomware deployed against an unnamed U.S.-based company, adding it found no branding or overlaps that connect it to any previously known ransomware actors.