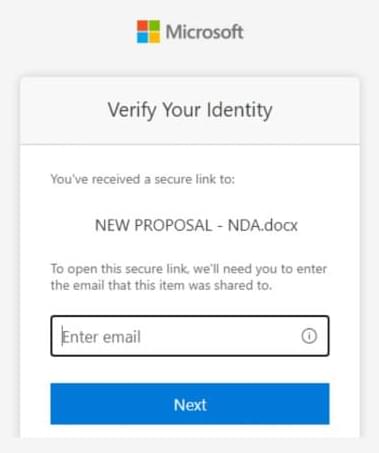
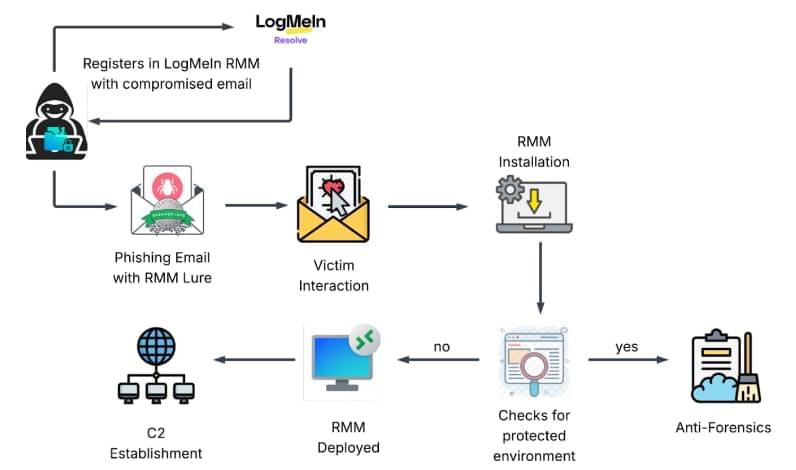
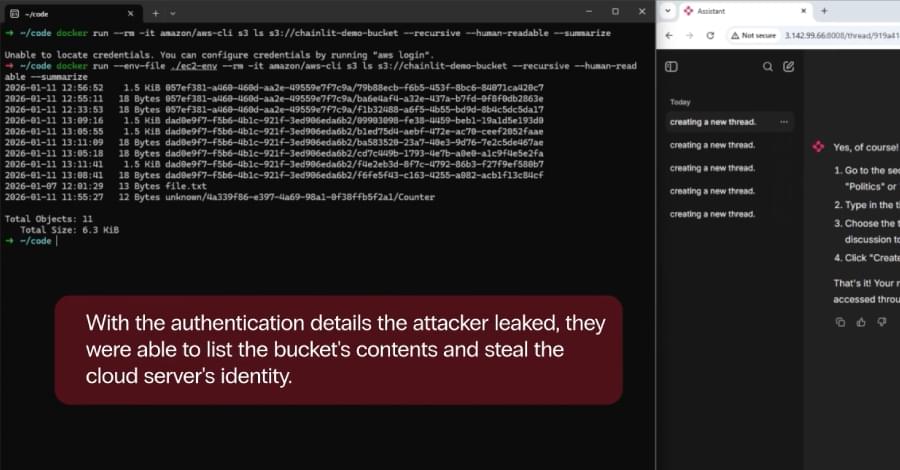
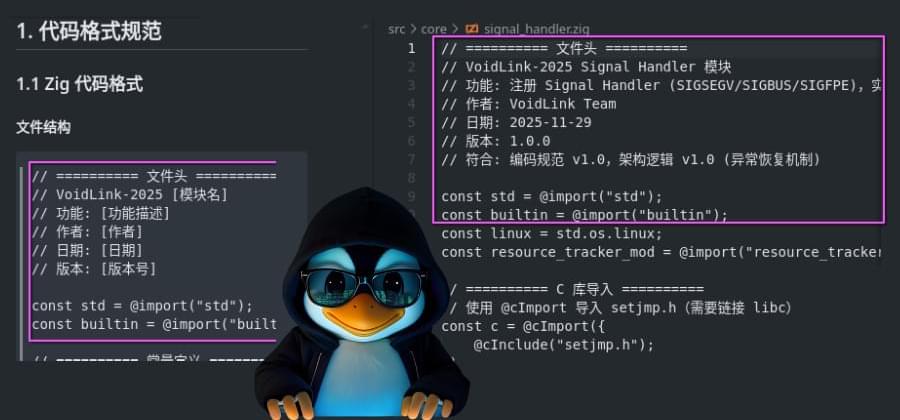
In my latest Forbes article, I explore one of the most critical questions facing leaders today:
How do we use AI to augment human intelligence rather than diminish it?
AI’s true power isn’t about automation alone—it’s about amplifying human judgment, creativity, and decision-making.
#AI #HumanCentricAI #artificialintelligence #tech #AugmentedIntelligence #Forbes #Leadership #Cybersecurity #EmergingTechnology #DigitalTransformation
Human-centric AI is the new frontier; it is not AI against human intelligence, but AI with human intelligence.