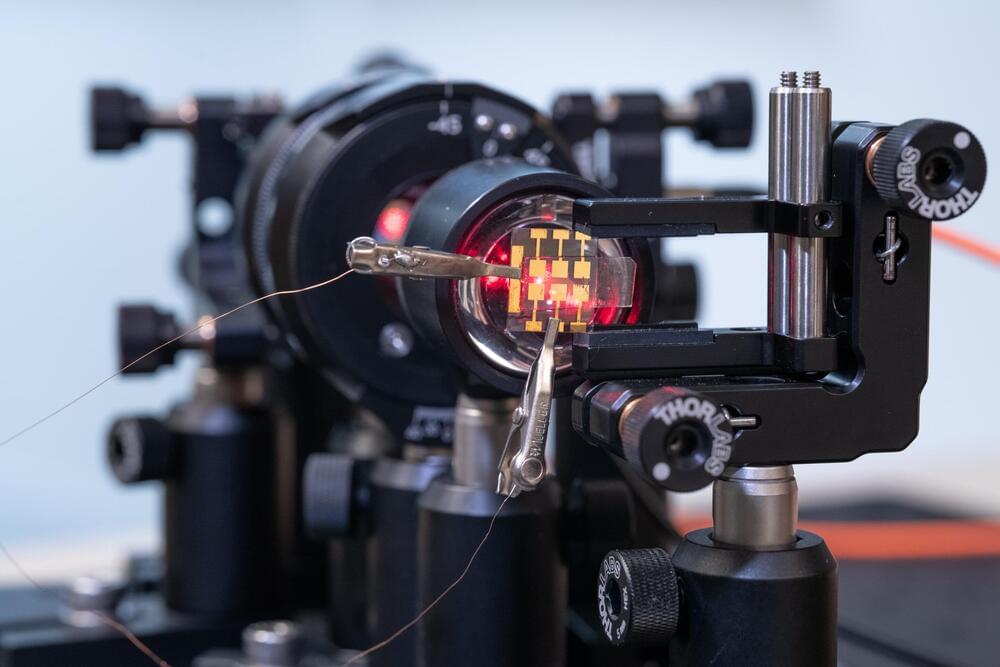
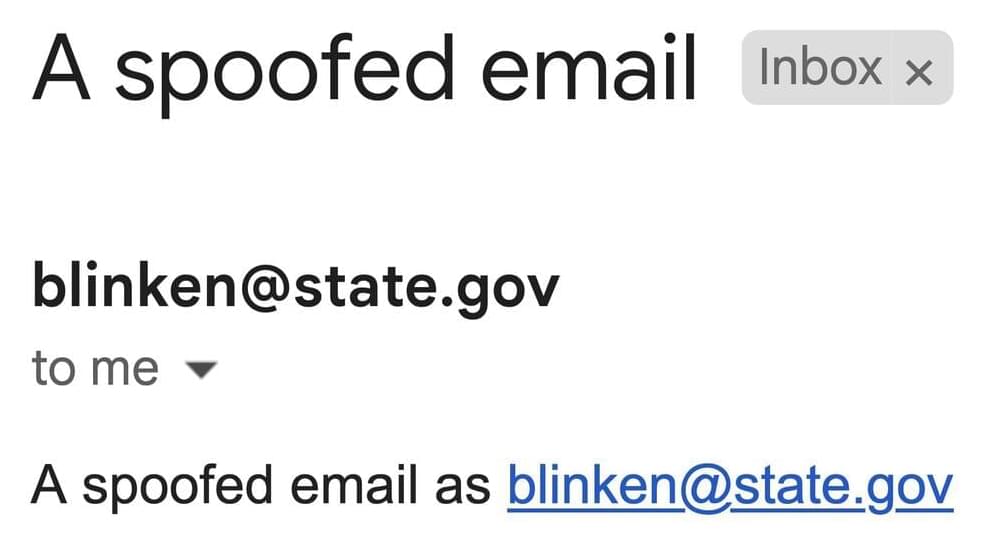
China-backed hackers stole a digital skeleton key allowing access to US government emails.
To recap, Microsoft disclosed in July that hackers it calls Storm-0558, which it believes are backed by China, “acquired” an email signing key that Microsoft uses to secure consumer email accounts like Outlook.com. The hackers used that digital skeleton key to break into both the personal and enterprise email accounts of government officials hosted by Microsoft. The hack is seen as a targeted espionage campaign aimed at snooping on the unclassified emails of U.S. government officials and diplomats, reportedly including U.S. Commerce Secretary Gina Raimondo and U.S. Ambassador to China Nicholas Burns.
How the hackers obtained that consumer email signing key was a mystery — even to Microsoft — until this week when the technology giant belatedly laid out the five separate issues that led to the eventual leak of the key.





 עברית (Hebrew)
עברית (Hebrew)