Ransomware attackers targeting a Fortune 100 company in the finance sector used a new malware strain, dubbed PDFSider, to deliver malicious payloads on Windows systems.
The attackers employed social engineering in their attempt to gain remote access by impersonating technical support workers and to trick company employees into installing Microsoft’s Quick Assist tool.
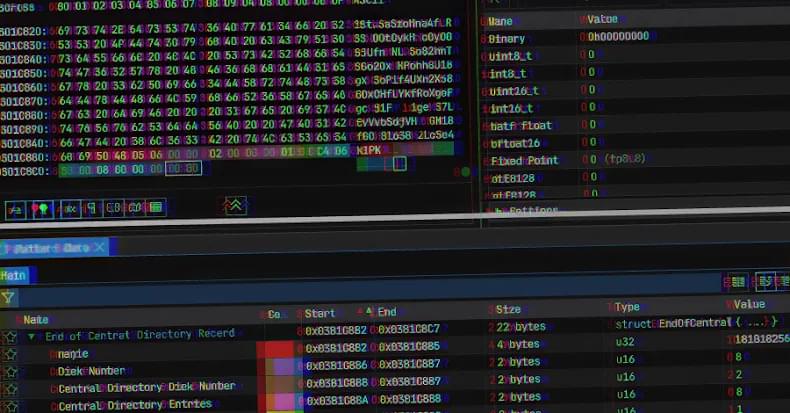
Researchers at cybersecurity company Resecurity found PDFSider during an incident response and describe it as a stealthy backdoor for long-term access, noting that it shows “characteristics commonly associated with APT tradecraft.”