Experts say the VoidLink Linux malware was largely built using AI, reaching 88,000 lines of code in days and highlighting faster malware development.


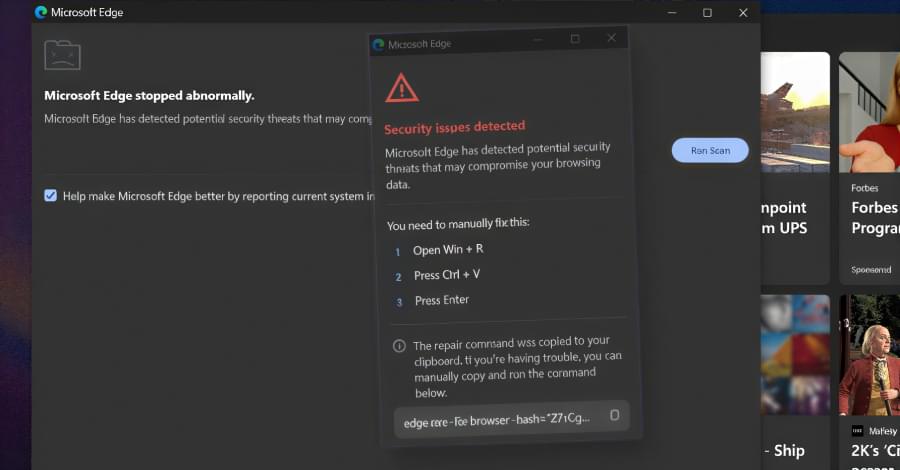
People worldwide are being targeted by a massive spam wave originating from unsecured Zendesk support systems, with victims reporting receiving hundreds of emails with strange and sometimes alarming subject lines.
The wave of spam messages started on January 18th, with people reporting on social media that they received hundreds of emails.
While the messages do not appear to contain malicious links or obvious phishing attempts, the sheer volume and chaotic nature of the emails have made them highly confusing and potentially alarming for recipients.

A new family of Android click-fraud trojans leverages TensorFlow machine learning models to automatically detect and interact with specific advertisement elements.
The mechanism relies on visual analysis based on machine learning instead of predefined JavaScript click routines, and does not involve script-based DOM-level interaction like classic click-fraud trojans.
The threat actor is using TensorFlow.js, an open-source library developed by Google for training and deploying machine learning models in JavaScript. It permits running AI models in browsers or on servers using Node.js.


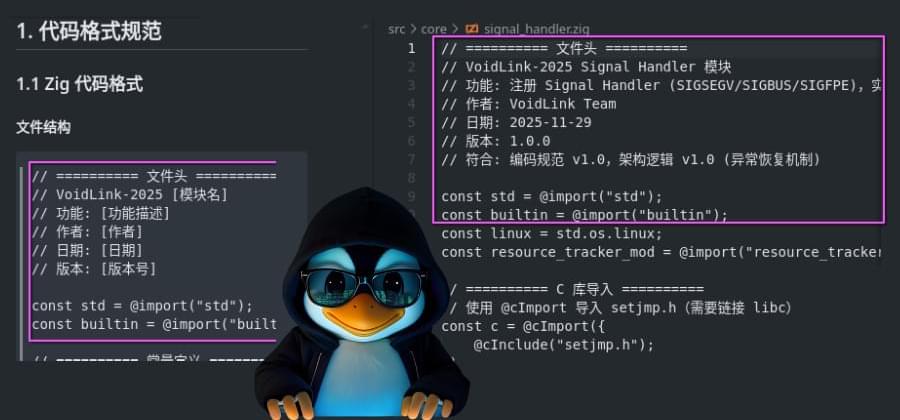
The recently discovered cloud-focused VoidLink malware framework is believed to have been developed by a single person with the help of an artificial intelligence model.
Check Point Research published details about VoidLink last week, describing it as an advanced Linux malware framework that offers custom loaders, implants, rootkit modules for evasion, and dozens of plugins that expand its functionality.
The researchers highlighted the malware framework’s sophistication, assessing that it was likely the product of Chinese developers “with strong proficiency across multiple programming languages.”
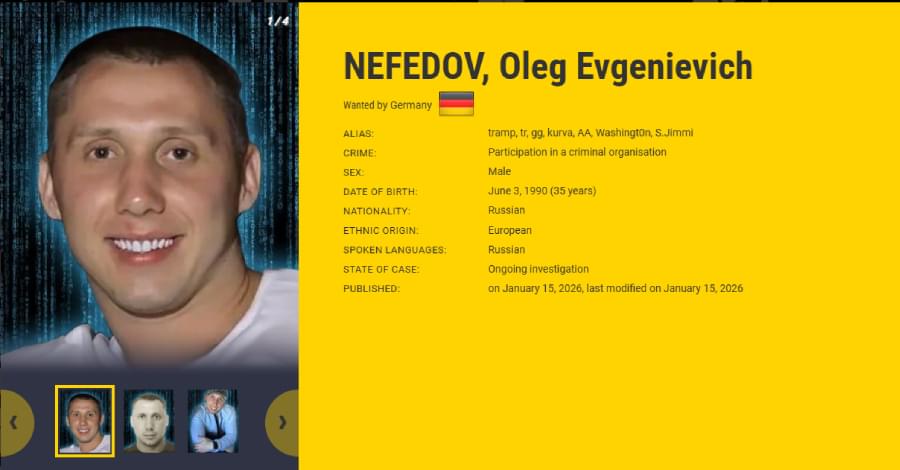
Ukrainian and German law enforcement authorities have identified two Ukrainians suspected of working for the Russia-linked ransomware-as-a-service (RaaS) group Black Basta.
In addition, the group’s alleged leader, a 35-year-old Russian national named Oleg Evgenievich Nefedov (Нефедов Олег Евгеньевич), has been added to the European Union’s Most Wanted and INTERPOL’s Red Notice lists, authorities noted.
“According to the investigation, the suspects specialized in technical hacking of protected systems and were involved in preparing cyberattacks using ransomware,” the Cyber Police of Ukraine said in a statement.

Information technology giant Ingram Micro has revealed that a ransomware attack on its systems in July 2025 led to a data breach affecting over 42,000 individuals.
Ingram Micro, one of the world’s largest business-to-business service providers and technology distributors, has over 23,500 associates, more than 161,000 customers, and reported net sales of $48 billion in 2024.
In data breach notification letters filed with Maine’s Attorney General and sent to those affected by the incident, the company said the attackers stole documents containing a wide range of personal information, including Social Security numbers.
Malicious Chrome extensions on the Chrome Web Store masquerading as productivity and security tools for enterprise HR and ERP platforms were discovered stealing authentication credentials or blocking management pages used to respond to security incidents.
The campaign was discovered by cybersecurity firm Socket, which says it identified five Chrome extensions targeting Workday, NetSuite, and SAP SuccessFactors, collectively installed more than 2,300 times.
“The campaign deploys three distinct attack types: cookie exfiltration to remote servers, DOM manipulation to block security administration pages, and bidirectional cookie injection for direct session hijacking,” reports Socket.